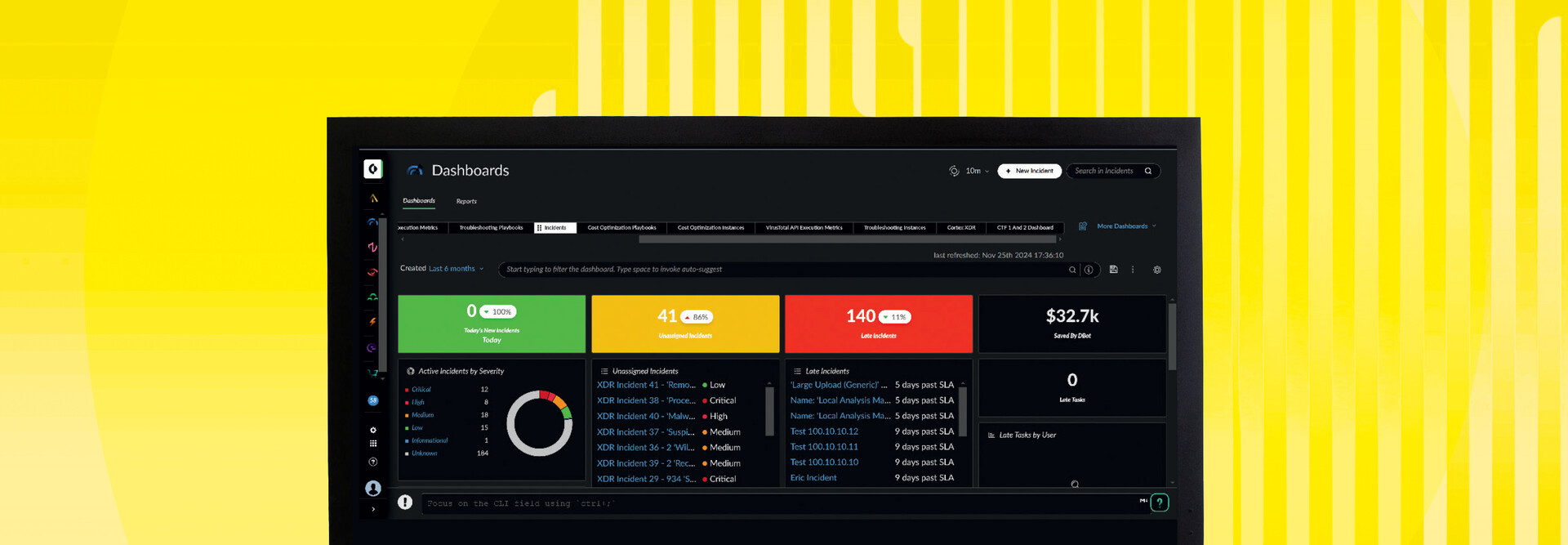
Zscaler Makes It Simple to Access Internal Resources
Unlike a traditional VPN, ZPA does not require users to connect to a network or establish direct paths to internal resources. As a software-defined, cloud-based solution, ZPA provides secure access to internal applications without placing users on the network. It uses an identity- and context-based authentication model to connect to critical resources, based on zero-trust principles to ensure data security and integrity.
Because ZPA separates application access from network access, it reduces any attack vector and the overall vulnerability surface, minimizing lateral movement. This capability empowers networks with a key security advantage for handling sensitive data, and it supports access to applications across multicloud environments, data centers and hybrid architectures, which makes it ideal for FSIs with complex IT environments.
Since ZPA will only secure users with access to authorized applications based on contextual factors such as identity and location, it’s compliant with the Cybersecurity and Infrastructure Security Agency’s Zero Trust Maturity Model. This model carries a stringent identity verification and continuous monitoring process, which ZPA easily achieves.
Work on the go and from remote locations will continue to present nightmares for many IT security teams. But with security applications such as Zscaler, CISOs can rest easier knowing their businesses are better protected without compromising operations and productivity.
SPECIFICATIONS
PRODUCT TYPE: Cloud-based zero-trust network access solution
VERSION: Professional Edition
SOFTWARE TYPE: Subscription
SOFTWARE SUBTYPE: Online and appliance-based services
LICENSE: Annual, per user
Key Challenges Users May Face When Implementing Zscaler
While ZPA offers numerous advantages, there are some implementation considerations that FSIs must consider in order to drive even more success and efficiency.
The first consideration is the journey IT teams need to account for when transitioning from legacy VPNs and perimeter-based security over to ZPA. This migration requires careful planning, especially for large businesses with aging infrastructure. The planning should include an effective communication strategy for users as well as training. Using ZPA is a lot easier than fiddling with VPNs, but it is quite different from what users have been doing with their legacy infrastructure.
It also helps if organizations validate all of their identity information as part of the inventory of app mapping. This step should also include mapping access patterns to feed into new security policies. Since ZPA’s policy model may require security and IT teams to adopt new processes, it’s essential that training and support from Zscaler be extended to IT implementation teams as well. This is an essential step for a smooth initial rollout.
As tough as it is to take some of these steps, the performance and security that they support are worth it. FSIs with remote operations around the world or those that are distributed across large networks will find a lot of benefit from ZPA due to its architecture, which is built on Zscaler’s Security Service Edge platform. This platform provides consistent application performance regardless of user location by leveraging a global cloud infrastructure with over 150 data centers. Because of that, whether users are in Washington, D.C., or the Hawaiian Islands, they will always have secure and fast access to the data and applications that they need to do their jobs.
EXPLORE: The security solutions and services that can protect organizations from attacks.