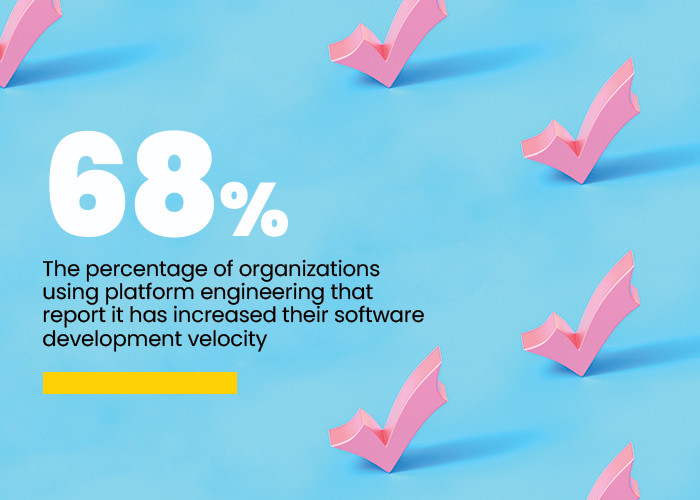
As organizations aim to design, build and maintain software development tools more efficiently, they must incorporate security as a key component in this platform engineering process.
A recent IDC survey shows that security and compliance guardrails are the top capabilities that DevOps professionals want their platform engineering teams to provide.
“One of the core benefits of platform engineering is that it forms a bridge between the needs of developers and security teams to bake security into the DevOps pipelines they provide as a service,” says Jim Mercer, program vice president for Software Development, DevOps and DevSecOps at IDC.
Fernando Montenegro, senior principal analyst for cybersecurity infrastructure security intelligence service at Omdia, believes platform engineering will make implementing security practices more “seamless” for developers.
“To do that, and to protect the platform itself against threats from attackers, it is critical that organizations include security stakeholders in the design, implementation and operation of modern platforms,” he says.
Here are some ways IT leaders can ensure that security is part of the platform engineering process.
Click the banner below to improve your workflows with platform engineering.
Don’t Neglect Security in Your DevOps Process
Enterprises must protect their digital assets, especially interconnected systems, applications and data repositories. Strategies include identity and access management, a framework for controlling access to applications in which individuals and devices only receive access to the appropriate data and applications.
“Organizations are ultimately responsible for their own software delivery and their own code,” says Paul Nashawaty, practice leader and lead principal analyst at the Futurum Group.
He adds that end users expect organizations to protect this code within reason. Businesses often release code without proper testing. Therefore, platform engineering teams should work with development teams to ensure that code is protected.
Strategies to protect code include a software bill of materials, a list of ingredients in a software package being delivered. A software bill of materials “gives you a blueprint or a template for what should be in there,” Nashawaty explains. “And if there’s more in there, that’s a red flag, so it allows for actionable insights for the platform engineering team to take immediate action.”
Nashawaty compares it to a baker adding sardines into a cake: It’s not in the recipe. “If platform engineering teams notice additional components that should not have been included, they can flag it to security teams,” he says.
In May 2021, the White House issued an executive order on improving the nation’s cybersecurity. It outlines how to protect code before it is shipped to the public.
“It requires the checks and balances from the organization to ensure that it’s delivering safe code and safe applications,” Nashawaty says. “That’s where platform engineering comes in.”
Build Cyber Resilience with Deliberation and Security Automation
Testing code slowly is essential, Nashawaty says.
“You have to slow down, test code, ensure it’s proper, and then you can go faster,” Nashawaty says. “Otherwise, your reputation is at risk, you’re compromising your clients, you’re jeopardizing your business, and ultimately, it could end in very poor results for your organization.”
He advises companies to use “trusted code from trusted repositories” as part of a zero-trust strategy, in which IT leaders continuously verify users accessing a network.
To improve an organization’s security posture over time and maintain cyber resilience, organizations should also consider automating security testing, vulnerability scanning and compliance checks.
“Security automation is indeed critical for scale,” Montenegro says. Security should be a key component of the automation workflow and a routine part of the build process, he suggests.
“This is much better than forcing developers to manually call security tests, for example.”
Click the banner below to learn why cyber resilience improves threat defenses.
Shore Up the Software Development Lifecycle
In the software development lifecycle, organizations should move security checks closer to day zero or day one of development rather than waiting until release day, Nashawaty advises.
“You need to have security checkpoints along each stage of the pipeline,” he says.
Nashawaty recommends a sprint release as part of an agile software methodology, which involves iterative changes, versus a waterfall cadence, which happens over a period of time.
“Most modern software development cycles within platform engineering are leveraging agile development methodologies over waterfall, and they do that because it allows for faster iterations and faster changes,” he says.
Agile software development is more secure because organizations can address security issues immediately instead of waiting six months for the next release, Nashawaty says.
READ MORE: See how businesses are keeping their endpoints secure.
A key challenge for platform engineers is modernizing legacy applications, which include security holes.
“Platform engineers and CIOs have a responsibility to modernize by bridging the gap between the old and new and understanding the security implications between the old and new,” he says.
When securing the software development lifecycle, organizations should secure both continuous integration and continuous delivery/continuous deployment pipelines as well as the software supply chain, Mercer says. Securing applications entails “integrating security into the CI/CD pipelines in a seamless manner that does not create unnecessary friction for developers,” he says.
In addition, organizations must prioritize educating employees on how to secure applications and software supply chains.
“For example, while most organizations are familiar with traditional application security testing tools, many still do not understand how to secure their software supply chains properly,” Mercer says.
As part of baking security into the software development process, security responsibility shifts from the cybersecurity team to the development organization. That means security becomes as much a part of deliverables as quality or safety, Montenegro says.
“We see an increasing number of organizations adopting a security mindset within their engineering teams where the responsibility for product security lies with engineering, not the security team,” he says.
Going forward, incorporating security into the software development lifecycle will require close collaboration between developers and engineering teams, according to Montenegro.
“Just as development organizations translate business requirements into different aspects of the system they create, they need to do the same for security requirements,” he says. “They can work alongside security teams for collaboration, but we feel that this will increasingly become part and parcel of development and engineering.”