Primer, a startup company focused on artificial intelligence, has flourished in recent years, attracting big-name customers in areas like retail and national defense. As the company has matured, its customer base has grown, and its employee count has increased. Primer’s IT security team felt it was time to make cybersecurity improvements.
In October, the 7-year-old San Francisco-based company deployed new next-generation endpoint security software from CrowdStrike that protects both employee laptops and cloud workloads in Amazon Web Services and Microsoft Azure.
Primer also subscribed to CrowdStrike’s Falcon Overwatch managed detection and response (MDR) service, which includes network and endpoint monitoring by CrowdStrike security experts, who alert IT staff to real-time threats.
“This has taken us to the next level,” says Andre Aponte, Primer’s senior manager for security compliance. “It brings us so much more visibility at a much more granular level within our cloud production and user endpoints, and it brings it all under a single pane of glass.”
Click the banner to unlock exclusive security content when you register as an Insider.
As cyberthreats evolve and grow more sophisticated, endpoint security solutions are a critical line of defense against ransomware, malware and other cyberattacks.
Analysts say that’s especially true with the increase in remote work and the use of mobile and cloud computing, which requires businesses to go beyond perimeter-based security.
“The endpoint is the on-ramp for the corporate infrastructure, a purpose it serves for both the legit employee and for any crook that seeks to take advantage of that person’s access rights,” says Rik Turner, a senior principal analyst for cybersecurity at Omdia. “Human curiosity is such that phishing emails continue to circumvent corporate defenses, making the endpoint the weakest link and a logical target for attackers.”
READ MORE: How to protect networks with next-gen endpoint security.
Modern endpoint security solutions today go beyond traditional anti-virus signatures and use artificial intelligence (AI) and behavioral analytics to proactively detect threats, spot suspicious activity and block attacks.
They secure computers, servers and mobile devices, but endpoint security vendors are increasingly adding more capabilities in the form extended detection and response to also protect cloud workloads, the network, email and identity management, Turner says.
Cloud-Based Endpoint Security Keeps Devices Safe
Primer uses AI and natural language processing to analyze vast amounts of data and provide its customers with real-time actionable intelligence, so securing customer data is critical. Protecting endpoints used by the company’s 130 employees, most of whom work remotely, is key, Aponte says.
Last year, Primer needed to upgrade its endpoint security because its existing anti-virus software was taking up too many computing resources on employees’ Apple MacBooks and Microsoft Windows notebooks, making it difficult for them to work, says Chad Boyd, Primer’s staff security engineer.
DIG DEEPER: Find out why next-generation endpoint security is different.
The company needed a solution that was lightweight yet effective. It found that in CrowdStrike Falcon Complete, a cloud-based solution that protects employees’ computers and cloud workloads on Amazon Web Services and Microsoft Azure while providing endpoint detection and response, Boyd says.
“We can set up rules, so when it sees a certain type of suspicious activity, it stops it,” Aponte says. “It’s a force multiplier. It helps us because we have a fairly small security team.”
Credit Union Secures Virtual Desktops
In Arlington, Va., the United States Senate Federal Credit Union deploys the cloud-based Carbon Black security solution by VMware to protect its virtual desktops and servers in its two data centers in colocation facilities.
Using Dell hardware, the credit union, which has about 135 employees at its headquarters and four branch locations, is standardized on VMware’s full stack of IT infrastructure software, so it made sense to include the Carbon Black Endpoint and Carbon Black Workload solutions, says CIO Mark Fournier.
“We like that it’s part of the broader ecosystem,” Fournier says, noting that he can manage and monitor the organization’s entire environment, including endpoint security, from VMware’s vCenter dashboard. “For companies that are already capitalizing on different parts of the VMware operations stack, this is a good option for endpoint security.”
EXPLORE: Learn why organizations need a security strategy for multi-cloud operations.
The cloud-based software goes beyond virus and malware signature files and uses AI-powered analytics to identify malicious behavior and block attacks, he says.
Last fall, the credit union began using the Carbon Black Managed Detection and Response service. Like Primer, it is benefiting from 24/7 expert monitoring.
“It leverages machine learning to intelligently sort through and filter out the alerts, so the Carbon Black team can tell us, ‘Hey, here are the ones you need to look at,’” Fournier says. “It enables our team to focus on what we should take action on.”
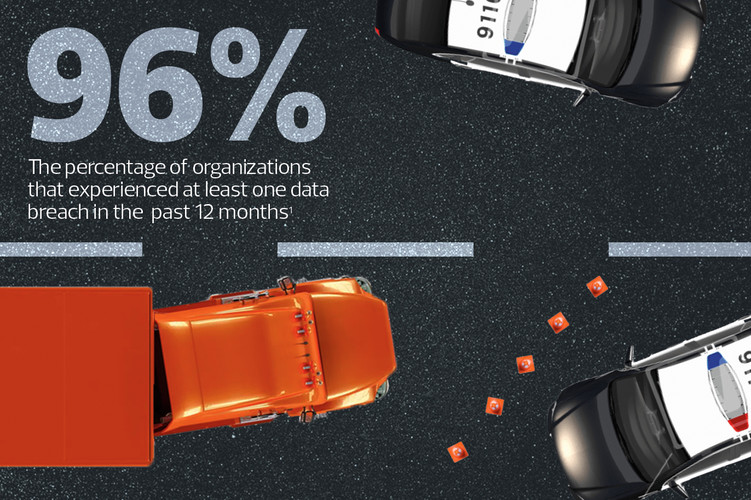
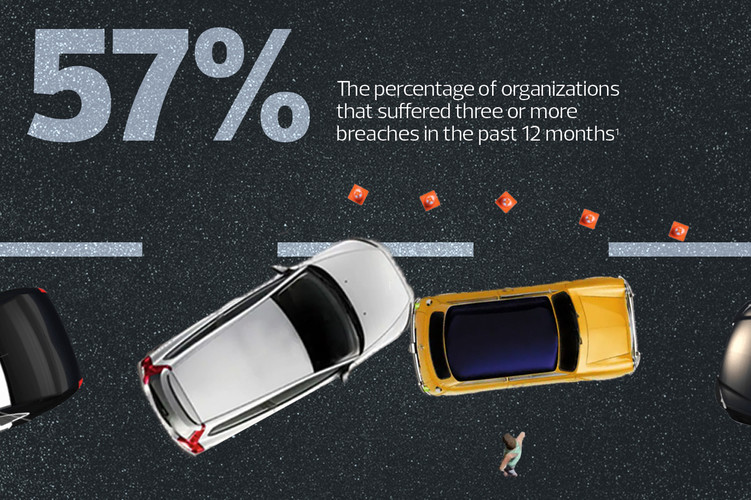
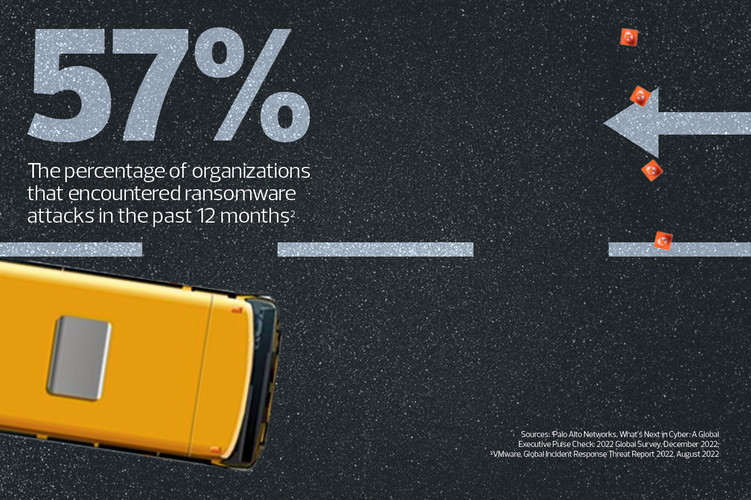
57%
The percentage of organizations that suffered from ransomware in the last year.
Source: VMware, “Global Incident Response Threat Report 2022,” August 2022.
One Cybersecurity Solution Rises Above Another
In San Diego, GoodFarms, which produces and distributes fruits and vegetables, has used Malwarebytes endpoint security for the past nine years. The solution has proven itself repeatedly, says IT Director Nelson Estrada.
In fact, five years ago, the company’s secondary data center, which used a different endpoint security solution, went down because of a ransomware infection. Fortunately, the ransomware didn’t infect GoodFarms’ main data center since it was protected by Malwarebytes. After that, the company deployed Malwarebytes in both data centers.
“We used a different tool in one data center, and it got ransomware,” Estrada says. “We have Malwarebytes in the other, and nothing happened. For me, that proves it works.”
DISCOVER: Find out how to keep ransomware at bay with a smart backup strategy.
GoodFarms, which has about 300 employees, uses the security solution to protect employee devices, including HP desktop and laptop computers and iPhone devices.
Estrada likes the fact that the security vendor continually improves the product. Besides protection against malware and viruses, Malwarebytes has added other capabilities, including patch management and Domain Name System filtering, which allows him to block users from suspicious and inappropriate websites.
“I’m happy with Malwarebytes because it’s always evolving,” he says. “It’s like a Swiss Army knife and has everything in one solution.”