Mastering MDM with Windows Intune
As the use of mobile devices in different form factors increases, a strategy to keep them secure when accessing corporate data is paramount. Prior to the release of Windows Intune, Microsoft’s subscription cloud management and security solution for small and medium-sized businesses, comprehensive mobile device management (MDM) was reserved for organizations that could afford enterprise-class solutions, such as Microsoft’s System Center.
Windows Intune Goes Native
The latest update to Intune builds on existing capabilities for managing devices via Exchange ActiveSync (EAS) by providing direct (agentless) management of Windows Phone 8, Windows RT and Apple iOS devices. Direct management doesn’t require EAS and instead uses technology native to the devices. Support for Android and Windows Phone 7 devices is still provided via EAS.
The gradual move away from EAS allows organizations to leverage Windows Intune not only for device security, such as password policies and remote wipe, but also for managing applications. This provides a better user experience on the Windows Phone 8, RT and Apple iOS platforms. Other changes in Intune include integration with System Center Configuration Manager SP1 and per-user licensing for up to four devices.
Table 1 – Understanding how Windows Intune manages different mobile operating systems
| Operating System | Windows Intune Management |
|---|---|
| Windows RT | Direct |
| Windows Phone 8.0 | Direct |
| Apple iOS 4.0 or later | Direct |
| Windows Phone 7.0 or later | EAS |
| Android 2.1 or later | EAS |
Configuring Intune for Direct Management of Mobile Devices
Windows Intune must be set as the management authority for mobile devices, and once configured, this can’t be changed. You can set the management authority in the Intune Admin Portal (admin.manage.microsoft.com) from the Getting Started screen on the System Overview tab or under Tasks in Administration > Mobile Device Management.
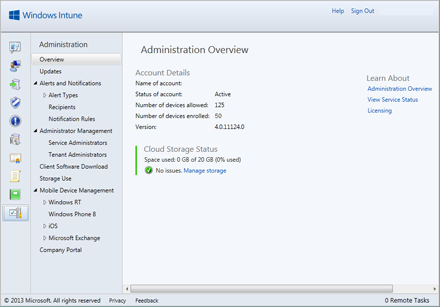
Figure 1 – Windows Intune Admin Portal
Once you’ve decided to make Windows Intune the management authority for your organization’s mobile devices, make sure that you have users provisioned in Windows Intune. Users can either be created manually in the Intune Account Console (note that accounts are not managed in the Admin Portal but in a dedicated console) or synchronized from your on-premise Active Directory to Windows Azure Active Directory, which Windows Intune can utilize for user account information.
Enroll Mobile Devices with the Intune Service
Mobile devices need to be enrolled with the Intune service before applications can be deployed or policies applied. The simplest way to do this is to provide users with a link to Microsoft’s enrollment server.
Supported devices can be set to automatically discover an Intune enrollment server, so users don’t need an enrollment server URL. For automatic discovery, you need to create a CNAME DNS record to redirect your custom Windows Intune domain to Microsoft’s enrollment server. For example, you might create a CNAME record in your DNS to redirect enterpriseenrollment.myintunedomain.com to enterpriseenrollment.manage.microsoft.com, where mytintunedomain.com is replaced with your own domain name.
The enrollment process varies between devices but to enroll from Windows Phone 8, select Company Apps under Settings > System. Then choose Add Account and enter your company or Intune credentials. Once enrolled, you’ll be prompted to install the Company Portal App.
As part of enrollment, a mobile device management certificate is installed, which allows Intune to manage the device. An application enrollment token (AET) is also installed if the organization has followed the necessary steps to create an AET for distributing company apps. Enrolled devices contact the Intune management server every eight hours to check for app or policy updates. A hardware and enterprise app inventory are also sent.
Creating Mobile Device Policies
Create a policy in the Admin Portal using a simple wizard. A policy template for mobile devices can get you started quickly. You can also choose to create new policies with a series of recommended settings or choose your own. Policies are applied to Intune groups, which must be populated with users before a policy will be applied to a device.
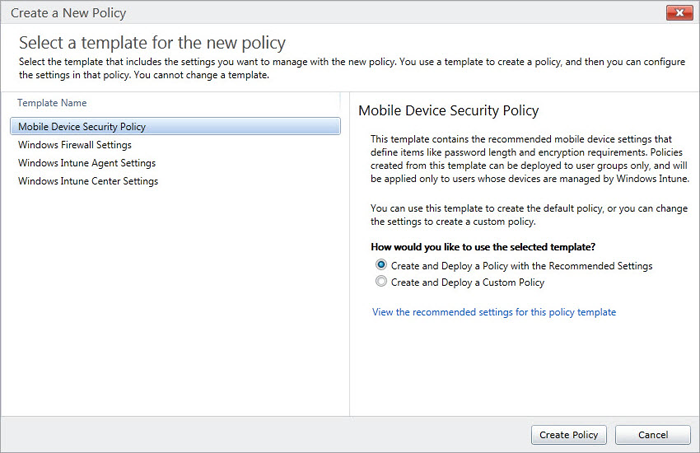
Figure 2 – Creating a Windows Intune policy to manage mobile devices
If you want to choose your own settings or change the recommended policy, settings are divided into password, device restrictions, e-mail and encryption categories. Any settings that apply only to specific devices are also singled out, making it easy to understand which configuration settings apply only to specific platforms.
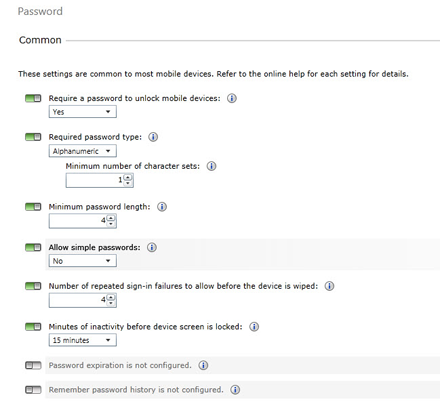
Figure 3 – Choosing mobile device password settings in Windows Intune
Distributing Apps to Mobile Devices Using Windows Intune
If you want to distribute company apps using the Intune service, you will need to apply for a Windows Dev Center subscription ($99/year) and an enterprise mobile code-signing certificate from Symantec ($299/year).
An AET must then be created with the AETGenerator tool, which is part of the Windows Phone SDK 8.0 and can be downloaded for free from Microsoft’s website (dev.windowsphone.com/en-us/downloadsdk). Windows Intune automatically deploys the AET to manage devices as they are enrolled.
Finally, developers must sign apps (XAP files) using a PFX file that is exported from the Symantec enterprise mobile code-signing certificate. Windows Phone SDK 8.0 provides command-line and PowerShell tools for this task.
The Takeaway for IT
While setting up Windows Intune for MDM isn’t a walk in the park, it’s not as complex if you don’t need to distribute company apps. Most important, Intune can directly manage critical security settings on most mobile devices without the configuring and distributing local agents, which in turn should decrease the total cost of ownership and improve security by providing greater assurance that policies are being applied successfully. And for those that need it, the ability to distribute company apps provides additional value.








