Patching known vulnerabilities has always been — and always will be — a core tenet of cybersecurity. However, new data from SonicWall suggests that small and medium-sized businesses will need to be more methodical and targeted in their patch management practices while also adopting a layered cybersecurity strategy.
In its 2025 Threat Brief, SonicWall notes that more than 6.9 million threats targeting Microsoft vulnerabilities were blocked by SonicWall firewalls in 2024, a 110% increase compared with 2023.
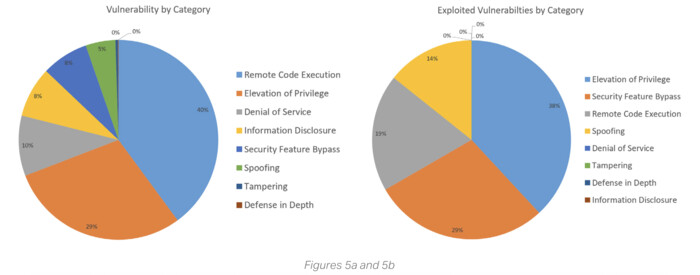
However, the most commonly patched vulnerabilities weren’t always the most exploited. Remote code execution flaws made up 40% of vulnerabilities but accounted for only 19% of exploits. By contrast, elevation of privilege bugs — which can be less visible but are often more dangerous — were the most exploited, accounting for 38% of real-world attacks.
“With over 1,000 vulnerabilities patched and millions of associated threats blocked, one thing is clear: Patching alone isn’t enough,” says Douglas McKee, executive director of threat research at SonicWall. “Attackers are moving faster than ever to exploit the paths that provide the most rewards and least resistance.”
Click the banner below for deeper insight into modern cyberresilience.
The Most Common Vulnerabilities Aren’t the Most Exploited
The clearest takeaway from SonicWall’s data is that patching the most common vulnerability types simply isn’t as effective as it used to be. The report indicates that, in the wild, hackers flock to what works.
For example, security feature bypass methods accounted for just 8% of known vulnerabilities but represented 29% of exploits.
Image courtesy of SonicWall
These figures are a reminder that volume alone cannot determine patching priorities. Instead, SMBs should also be guided by how attackers behave in the real world. This requires a more circumspect approach to gathering and analyzing threat intelligence, and taking measures based on the data.
Vulnerability Severity Isn’t Always What It Seems
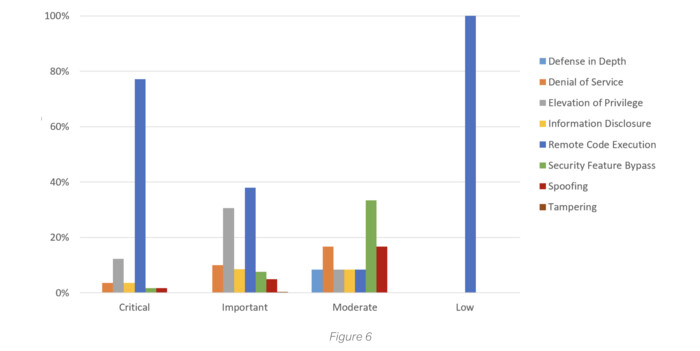
By volume, remote code execution vulnerabilities were the most common. They also accounted for 77% of the most critical vulnerabilities. But being both the most common and the most critical of vulnerabilities didn’t make them most likely to be exploited.
For example, security feature bypass flaws were less common and less critical in severity than remote code execution vulnerabilities. However, SonicWall’s data revealed that they were frequently used to help attackers escalate access or disable security tools, and these actions can turn a moderate vulnerability into an exploit with critical consequences.
SonicWall also noted that Microsoft labeled 123 vulnerabilities as “Exploitation More Likely” in 2024, which is an important indicator for cyberdefense. However, only 10 of those made it into the Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities Catalog. Two of those 10 had been labeled “Exploitation Less Likely,” demonstrating that even the best predictions can be undone by real-world cybercriminal behavior.
Image courtesy of SonicWall
Layered, Proactive Defenses Have Become Mandatory
Microsoft’s 2024 vulnerability landscape reflected the variety and volatility of cyberthreats over sheer volume. Patching is (and always will be) important, but figuring out how to prioritize patches is becoming more complicated.
“Businesses need a smarter, faster approach, one that blends real-time detection and response with layered defenses across every attack surface,” McKee says. He flagged the following as priorities:
- Identifying sophisticated privilege escalation attempts
- Neutralizing malware hidden in Microsoft Office documents
- Blocking exploits before they ever reach users
- Having integrated protections across endpoints, email accounts and networks
“Businesses that invest in coordinated, intelligence-driven security aren’t just keeping pace with threats, they’re staying ahead of them,” McKee says. “That can often be the difference.”
UP NEXT: Why a managed security service provider is essential for small businesses.