Small Businesses Redouble Defenses to Combat Growing DDoS Attacks
They’re out there. Ben Warriner has seen them storming the firewall at Wade Ford. But the business operations manager at the Smyrna, Ga., car dealership has managed to keep the distributed denial of service attacks off his network using strong border security tools.
“They’ve kept us safe,” he says, “so far.”
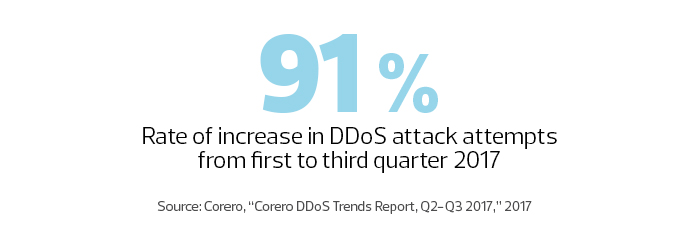
DDoS attacks have been around for decades, and while they might not generate the headlines today that ransomware and data theft do, they are a growing threat due in part to the explosion of the Internet of Things.
The attacks use malware or exploit weak or absent authentication credentials to take over computers, then direct them to generate enough traffic to slow or crash their targets.
Since IoT devices are essentially internet-connected computers — often lacking basic security — the volume of potentially exploitable equipment has mushroomed. Anything from a watch or camera to a baby monitor or thermostat can be hijacked into a DDoS botnet.
“There’s no big red siren on top of our building showing that these attacks are flying left and right,” says Brian Mengel, CTO for PenTeleData, a broadband internet service provider based in Palmerton, Pa. “But you never know when the next exploit of some IoT device is going to send traffic from 5 million smart devices to this target network to knock them offline.”
Another growth driver is the booming Malware as a Service market.
Cybercriminals sell DDoS attack kits for as little as $100, says Laura DiDio, principal analyst at Information Technology Intelligence Consulting.
“I don’t think people are taking it as seriously as they should be, because it’s really easy to find yourself under attack,” says Mengel. “It doesn’t cost an attacker very much to do this.”
Any organization is susceptible to a DDoS attack — or can become a pawn in one. Mengel tells customers in all industries to weigh the price of security measures against the cost of losing internet access for an extended period. Do employees sit idle?
Can remote doctors upload images to a hospital? Can bank branches process transactions? “What’s the real risk there?” Mengel asks.
With a layered defense, even a small business can thwart or mitigate an attack. DiDio likens it to protecting a home: A locked door, barking dog and blaring alarm can scare off a would-be burglar, but only if they’re in place before the thief arrives.
“If you’re not prepared, your network is going down, and it’s going down fast,” she warns.
SIGN UP: Get more news from the BizTech newsletter in your inbox every two weeks!
Segment Networks to Guard Against DDoS Attacks
Future Link IT, an Elgin, Ill.-based ISP, has seen plenty of DDoS attacks, particularly against its clients’ upstream providers. Then, in 2015, Future Link itself fell victim to one.
Fortunately, the company’s administrators were able to observe the traffic and identify the IP addresses (including one for its DNS server) affected by the attack, so they shut them down. They rerouted unused IP addresses to those services, but it still took more than two hours to get back online, recalls Future Link Sales Manager Chris Higgins.

Photography by Ryan Gibson
After that, the company installed multiple DNS servers and segmented its network so that if it were attacked again, it could stay online and limit the number of customers affected.
DDoS attacks hit businesses of all sizes across all industries, but because corporations often have stronger security, SMBs can be more attractive targets.
“We’ve definitely seen a rise in small and midsized businesses getting hit,” Higgins says. “It’s keeping us busy.”
He advises clients to have a redundant internet solution to fall back on if they’re attacked.
Higgins also stresses that all but the smallest businesses need a business-class firewall to differentiate legitimate traffic from cyberthreats.
As a managed service provider, Future Link offers its clients the Barracuda CloudGen MSP firewall, which Higgins says is good for SMBs because it’s a scalable solution that includes all the modules and subscriptions they need inside the firewall rather than charging for each piece separately. “If you’re not doing email or web or VPN security, you’re leaving pretty big holes in your network,” he says.
Upgrade Firewalls to Enhance Security
At Wade Ford, Warriner uncovered a big hole in the network: The old dealership management system was using public IP addresses — a good-enough reason to pull the network in-house.
As a dealership with a steady stream of financial transactions, Warriner wanted to build a business-class network — one with a security posture akin to that of a bank, but with flexibility. “The most secure system in the world is the most insecure one because everyone has to work around it since they can’t work within it,” he says.
The biggest problem with Wade Ford’s old network was that the dealership kept winding up on email blacklists. Warriner put a spam filter on the company’s outbound email server, so if a computer is infected, he can block it before it gets to anyone else on the network or onto a blacklist.
In August 2017, Warriner upgraded to the WatchGuard Firebox when his old firewall reached end of life after nearly four years. His advice when upgrading firewalls: “Figure out what you need, then get the next size up,” so it can handle the exponential growth of data without impeding performance. He also likes WatchGuard’s georestriction tool, which lets him block traffic from entire continents where the company doesn’t do business. “My firewall just rejects out of hand” any such traffic, he says.
Since taking control of the network and implementing security best practices, Warriner’s email woes have disappeared. “I’ve gone past the three-year mark now without turning up on a single email blacklist,” he boasts.
But, he adds, security is a moving target. Threats such as the Equifax breach and the March ransomware attack against the city of Atlanta — both in his neighborhood — are reminders that he can’t let down his guard. That’s what drove him to earn his Certified Ethical Hacker credential last year. “The whole concept is to try to attack your own network and then fix it and patch it,” he explains.
Businesses can hire such experts on a contract or project basis. One of the best defenses against a DDoS attack is a security audit, Warriner says.
He runs Tenable’s Nessus Professional vulnerability scanner internally and conducts external Payment Card Industry (PCI) audits. “Having that outside third party makes a huge difference,” Warriner says. And while the cost of that extra security can be a burden to small and midsized business, it’s money well spent. “The cost of an audit doesn’t even weigh into the cost of remediation if there is some sort of big breach.”
DDoS Attacks Evolve to Target Random Businesses
Working with PenTeleData’s ISP subscribers, Mengel has seen a shift in the types of DDoS attacks being launched. Four years ago, they tended to be small, targeted toward tech-savvy individuals (the result of an argument over online gaming, for instance) and easy to mitigate. Today’s attacks are larger and often aimed at random businesses.
“These all tend to be volumetric attacks where the goal is to overwhelm the capacity of the customer — our end user,” he explains. “Take a cable modem customer who has a 100-megabit-per-second downstream pipe. You send 101 megabits per second — well, you’ve basically knocked them offline.”
To provide relief for customers, PenTeleData began offering DDoS-mitigation capabilities to clients. “It’s kind of a two-pronged thing,” Mengel explains. “We’re protecting the end user who’s the target of the attack, but if the attack is of sufficient size — many multiple times what that customer’s capacity is — it runs the risk of overwhelming our backbone capacity.”
PenTeleData uses a service that analyzes traffic patterns to optimize its network. If it detects an attack in progress, it signals to Radware’s DefensePro client to begin a mitigation for that customer. The system then scrubs the traffic from the DDoS attack in Radware’s cloud-based data centers before passing the clean traffic back down to PenTeleData’s customer.
That has eliminated the drive-by effect of having an attack against one customer overwhelm PenTeleData’s backbone to the point of impacting other customers, says Mengel. Plus, he adds, the systems are all automated, so a mitigation can happen without a customer even knowing about an attack.
“That’s the goal,” he says. “To give that customer uninterrupted service.”








