Inside the Real-World Fight Against Ransomware
Reporters and news broadcasters at San Francisco public TV and radio station KQED are used to covering breaking news, important issues and crises facing the community, but in mid-June, a crisis hit closer to home: a massive ransomware attack that essentially knocked out the company’s IT infrastructure.
On the day of the infection, an IT engineer was leaving the office for the evening when she heard rumblings of connection issues with a financial database. She investigated and discovered that ransomware had encrypted the database and other servers. She began shutting down the corporate servers and network in an effort to contain the outbreak, but the damage was done.
“We did not have 100 percent encryption, but the process had started on about 80 percent of our computers,” recalls KQED IT Director John Reilly.
KQED operates its TV and radio stations on distinct Active Directory domains, so broadcasts stayed up and running. Because the nonprofit also backed up its data, it didn’t have to pay ransom to regain access to corporate systems. Nonetheless, it has taken months for the company to fully recover from the attack.
>>Download CDW's Cybersecurity Insight Report to learn more about how organizations are managing risk in the more effective ways.
The global ransomware threat has crippled many businesses by locking computer screens or encrypting files. The malware — spread through malicious email links and attachments, compromised websites and unpatched software — demands that companies pay a ransom to unlock their systems or files.
The largest attack occurred in mid-May, when WannaCry ransomware infected 100,000 organizations in 150 countries within a day. Although government agencies and security researchers warned against paying the ransom, the cybercriminals collected more than $100,000 within 11 days of the attack, according to media reports.
“We’ve seen a real uptick in ransomware incidents,” says Jonathan Katz, director of the Maryland Cybersecurity Center at the University of Maryland. “Part of this may be due to the increased prevalence of bitcoin, which provides a convenient payment mechanism for malware creators. Part of this is also copycat behavior. As people see that ransomware attacks are effective, they are more likely to attempt such attacks.”
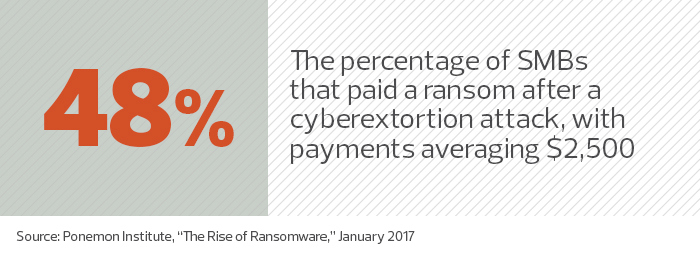
For small businesses, these attacks can spell literal doom. According to the “Second Annual State of Ransomware Report,” based on a survey by Osterman Research, 20 percent of U.S. small and midsized businesses had to close shop immediately after ransomware attacks.
Why Your Organization Needs Layers of Cybersecurity Defense
To guard against ransomware, companies are implementing best practices, such as installing the latest software patches, making backup copies of data and educating users on computer safety.
“You have to have multiple layers of security,” says Stuart Browy, security engineer at a pharmaceutical benefits company in Morrisville, N.C. “You not only have to stop attacks at the front door, you have to catch them if they make it through.”
To that end, many businesses have begun deploying advanced security tools, including endpoint security software that specifically protects against ransomware, along with file integrity monitoring tools that alert IT staff if ransomware begins encrypting files.
KQED only recently has begun to layer on security. When Reilly arrived at the nonprofit two years ago, he joined a culture that was driven by end-user mandates rather than a focus on security. Since the ransomware attack, however, management has given him the green light to beef up security, as well as a budget for new technology and additional IT staff, including a security engineer.
“If nothing ever breaks, people think IT is not important, but we found out in a big way that IT is everything,” Reilly says.
The ransomware infection this summer was a zero-day attack caused by a Samas ransomware variant that attacked newer versions of Microsoft Windows. It encrypted most of the organization’s 100 servers and many of its 400 desktops and notebooks. The cyberthieves behind it asked for a ransom of 1.7 bitcoins per device, or a total of 12 bitcoins (almost $70,000) to decrypt all affected systems.
Reilly says it’s unclear how the infection began. Any one of KQED’s 305 full-time employees or nearly 200 part-time staffers and interns could have introduced the ransomware. A visitor could have also caused the attack by connecting an infected computer to the network.
Immediately after the infection, the eight-person IT team and other engineering teams shut down all servers and computers. Previously taped radio shows were inaccessible, so radio hosts had to come in and do their broadcasts live the next day.

The IT team worked 16-hour days for the next week. They quickly wiped and refreshed notebooks and gave employees restricted Wi-Fi access so they could work. Then Reilly and his staff spent the next few months rebuilding servers and restoring data from tape backups, and deploying new security measures and technology to protect KQED from future threats.
“We had to rebuild in containment mode, so we let employees use Wi-Fi to access the internet without the ability to talk to each other or with servers,” Reilly says. “For the most part, people could get the bulk of their work done as long as they had internet.”
Deploy Advanced Security Tools and Segment the Network
To prevent another attack, Reilly bought the Carbon Black suite of products (Defense, Protection and Response), featuring next-generation anti-virus software that uses both signature-based and behavioral analysis to spot suspicious activity and block zero-day attacks before they compromise systems. KQED needed new security software because traditional anti-virus software typically doesn’t catch malware without known signatures.
KQED also segmented the network. The tech team physically separated parts of the network based on departments and workflows, creating logical separations through virtual LANs and using Access Control Lists on networking equipment to limit users to the portions of the network they need.
“There was a time when people said they needed access to everything, but in reality, they only need access to particular workflows and the printer that’s closest to them,” Reilly says. As IT staff restored servers, they gave users access to enterprise applications, but by using network-segmented “islands,” they restricted them to just a small portion of the corporate network.
“Now that we’ve done physical and logical segmentation of the network, if we have another attack, it will only infect a smaller segment of the organization,” Reilly adds.
Stay on Alert for Malware Intrusions
To protect against ransomware, businesses need to stay on top of patching to keep OSs and software current, Browy says. WannaCry was dangerous because it exploited vulnerabilities on older, unpatched Windows systems, which allowed it to propagate without human intervention, he says.
Browy says his company has avoided ransomware through the measures the company has taken. He regularly patches, runs endpoint security and monitors for intrusions.
He also has deployed Varonis Systems’ file integrity software on every server. If ransomware somehow sneaks past endpoint and perimeter defenses and starts encrypting files, Varonis DatAdvantage and DatAlert detects it and notifies Browy via email and text messages.

In cases he knows of, where affected data is critical or sensitive, companies have written scripts to automatically shut off servers to stop malicious encryption of files. For less critical data, IT administrators can investigate and manually intervene.
“If it’s a nonclustered primary server, you want that server to be automatically shut down immediately,” he says.
Data Backups Are Critical for All
Having a full backup of data and keeping it offsite is also an important line of defense against ransomware, says Chris Parker, founder of the popular WhatIsMyIPAddress.com website.
“Data backup is not prevention, but it allows you to recover from ransomware,” says Parker, who spent eight years as the IT director of an insurance brokerage firm.
Parker and his contractors practice good cyberhygiene, so he says his company is fairly secure. But no company is immune from an attack or disaster, so he abides by the best practice of maintaining three copies of his data, including copies stored offsite.
He copies his data to two USB drives. He keeps one at his home and stores the other at a bank. He also subscribes to Carbonite’s cloud storage service, which automatically backs up his hard drive. He suggests other small businesses do the same.
“If you are a small business, what would happen if your CEO couldn’t use his computer for a week?” Parker asks. “It’s worth it to spend the money to automatically store data offsite.”