In my testing, we set up a large test bed with mostly cloud-based assets as well as some on-premises servers, client machines and devices. The Tenable Vulnerability Management platform found over 1,400 potential vulnerabilities and designated 32 as critical, specifically flagging 14 that needed immediate attention. It provided a description of every vulnerability it located, the danger each represented, and instructions and advice on mitigation tactics.
Even large IT teams can struggle to keep track of every new vulnerability in complex networks these days. The Tenable Vulnerability Management platform can offer help, finding and fixing issues long before attackers can discover and exploit them.
SPECIFICATIONS
Product Type: Vulnerability Management Platform
Size of Known Vulnerabilities Database: 130,000 and constantly expanding
User Interface: Web-based portal
Distribution: As a Service through the cloud
Software Engagement Type: License per seat or user
Gain Access to In-Depth Security Dashboards
Tenable is well known for creating some of the best-looking and most easily accessible security dashboards in the industry. The company brings that same level of expertise to its vulnerability management platform. Not only can the dashboard work automatically based on both preset preferences and what it discovers through machine learning, it can also be manipulated to provide details about almost any aspect of the vulnerability landscape.
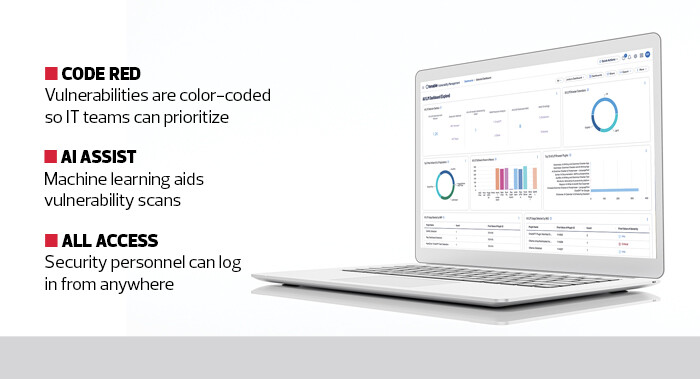
Without any prompting or help, the platform will display an informative dashboard that colorfully lays out the vulnerabilities hiding within a network. It’s extremely accurate at listing critical vulnerabilities that need immediate attention, coloring them red and grouping them from left to right based on severity.
Based on that, IT teams can prioritize their limited resources toward fixing a few dozen most dangerous problems mingling in with thousands of other, less problematic vulnerabilities.
But the Tenable platform can do much more than that. Users can slice that data however they like by setting up queries via a series of drop-down menus. For example, if you need to know if there are any breaches inside your network that are in the news, it can show you that. Users can also select broad categories of potential vulnerabilities, such as those that could provide access to critical assets, or those that are easy for attackers to exploit. You can even search for specific vulnerabilities by name and bring those to the surface.
Not only are vulnerabilities easy to search and see on the Tenable dashboard, they can also be filtered into reports that can be forwarded to others. In this way, IT teams can share security information with company officials who may not be as technically skilled but who can easily understand such reports. You can even configure those reports to fire off on a regular basis, a perfect way to demonstrate consistent progress to bosses over time.