Williams and his IT team researched several identity and access management solutions and soon chose OneLogin, becoming early adopters of multifactor authentication (MFA). There was some concern at the time about how the solution would be received, but those worries were soon dispelled, Williams says.
“Any initial doubt was overcome with additional training, both in person and prerecorded by our communications team,” he recalls.
Today, solutions such as MFA and single sign-on (SSO) are more widely recognized as cornerstones of a zero-trust security model.
Only the smallest companies, those “without a lot of intellectual property,” can “probably” do without MFA, says Jay Bretzmann, research vice president for identity, digital trust and cloud security at IDC. “But if they grow — if they become suppliers and have people logging in from different entities, for example — it becomes a different environment, and these tools become more necessary,” he says.
In reality, that characterizes most companies, which explains the rapid growth of MFA adoption, Bretzmann adds. Still, there’s plenty of room to expand. “If the market is about $20 billion now, when all is said and done it will be $100 billion,” he says.
Securing Growth at MillerKnoll
Everyday consumers encounter MFA when they interact with a business that requires additional verification information, such as a code sent by text or a fingerprint. SSO is another authentication strategy that allows known partners or employees to access a predefined set of applications, websites or data by logging in just once, whether they are in the office or working remotely.
Used together, these identity and access management tools greatly reduce the ability of bad actors to infiltrate a system.
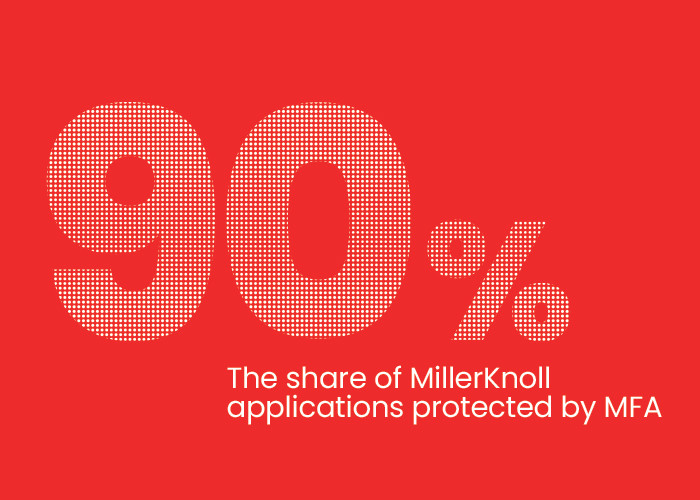
To combat bad actors directly, Williams and his team at MillerKnoll worked closely with OneLogin to deploy its MFA solution to the entire company, which now exceeds 23,000 users in more than 100 countries.
The company began with a phased rollout. “We had a large enough technical user base to ensure we caught any application compatibility issues immediately,” Williams says.
Additional training helped some users overcome their concerns that the new security measures would slow them down.
“I provided a multifactor roadshow to our separate business units, educating the users on not only the benefits of MFA to protect the enterprise but how it can protect their personal information,” he recalls. “This was also an opportunity to remind our user community of the basics of email security and best practices.”
Click the banner below to read the 2024 CDW Cloud Computing Research Report.