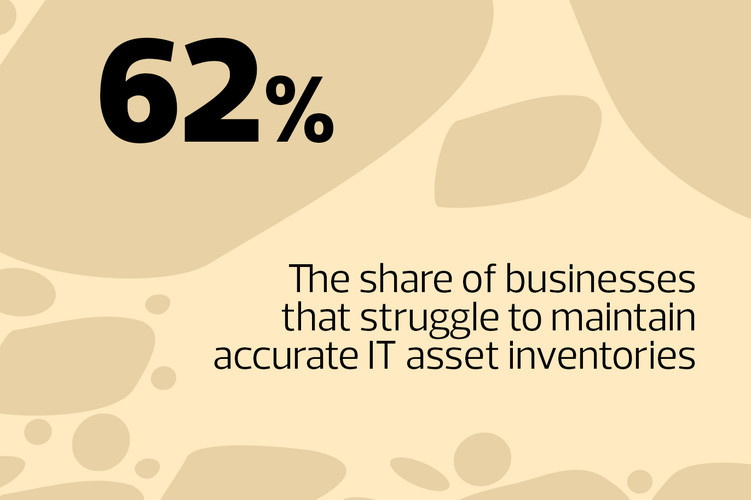
Businesses, particularly midsize enterprises, are increasingly adopting cloud-based unified endpoint management (UEM) software to centrally configure, control and secure a broad range of endpoint devices that run on different operating systems, such as PCs, tablets, smartphones and other Internet of Things (IoT) devices, analysts say.
Some use traditional software such as Microsoft Configuration Manager for PCs and more modern mobile device management software for mobile devices, says Gabe Knuth, a senior analyst with Enterprise Strategy Group.
Over time, MDM has evolved into UEM and come to encompass management of desktop PCs and laptops. UEM is gaining popularity because it unifies the management of PCs, mobile devices, applications and policies under a single console, Shelton says.
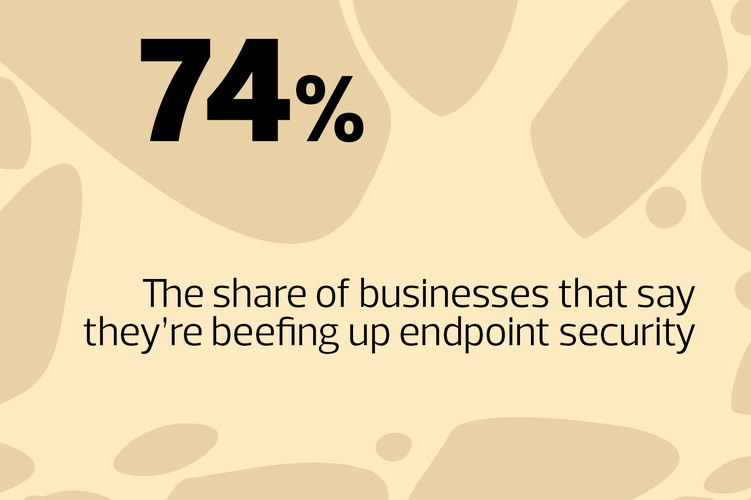
Providers are continually adding more advanced features to their UEM tools, including improved security, analytics and automation, Knuth says. Security is a huge piece of endpoint management. Some solutions add anomaly detection and risk scores, so IT staff can view the overall health of their devices and mitigate problems through a central dashboard.
“If you look at a Venn diagram of endpoint management and endpoint security, they’re overlapping more every day,” he says. Modernizing device management also simplifies device onboarding and remote support.