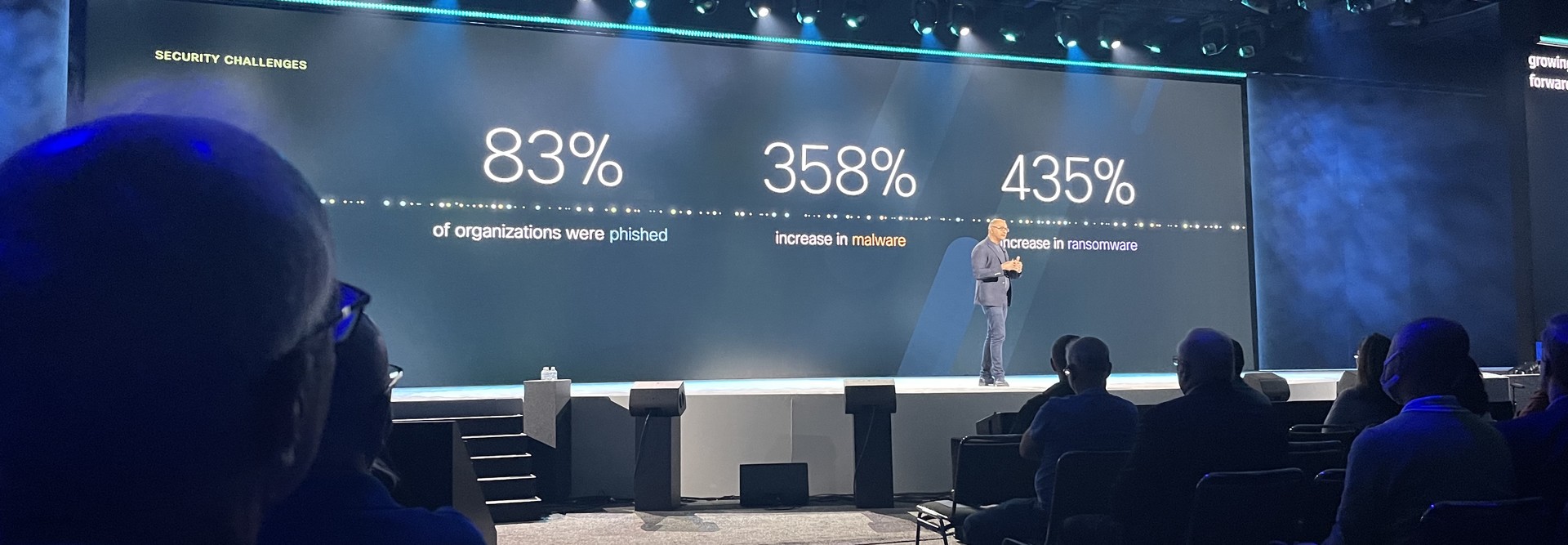
Security Strategy Should Consider Your Entire Business Ecosystem
“We, as businesses, are competing as holistic ecosystems, not as individual organizations by ourselves,” Patel said. “What that means is that you, yourself, might be materially impacted in the way that your production line works, the way that your supply chain works and the way in which your demand cycle works based on what happens to the other members in the ecosystem.”
Patel said the interconnectedness of business relationships now demands closer attention to access and identity management. “You don’t just have employees anymore. You have employees and contractors, but you have suppliers, customers and partners. And the amount of people that can impact your security posture is getting larger and larger.”
Each of these business relationships involves interaction with human beings, of course, and Patel noted that humans are easy targets for cybercriminals. “Attacks are becoming much more bespoke and personalized,” he said. “So, when you start thinking about these pieces, the way that we’re actually going out and attacking these problems is through zero trust.”
Still, according to Patel, even zero-trust policies need to evolve. It’s no longer enough to verify a user’s identity and access at the time of login; user behavior must be assessed regularly to continuously determine the level of access. “And if you’re doing something that's anomalous in nature, even though you might have logged in, even though you’d have access, I'm going to make sure I can understand.”
READ MORE: Learn how to overcome the challenges remote and hybrid work present.
Hybrid Work Continues to Introduce New Vulnerabilities
Business leaders acknowledge that remote and hybrid work are here to stay. Unfortunately, remote access will continue to make organizations less secure, according to Patel.
”When you actually see this mixed mode of working, what’s going to happen is you’re going to be accessing data and systems from any device, whether it be managed or unmanaged. You’re going to be accessing applications that are either sanctioned or not sanctioned, and you’re going to be accessing them from networks that are either secured or unsecured.”
This sudden increase in access necessitates a new security philosophy to minimize the risk to an organization’s intellectual property. Patel said organizations should be seeking fewer endpoint solutions and instead be looking to integrated architectures. “When I talk about integrated architectures, I'm talking about networking and security coming together, rather than being specifically separate islands by themselves. To simplify management, we need to make sure that management is simplified not just for the TechOps person but also the NetOps person, and ideally do it in a way that’s fluid.”
Most important, he said, it’s critical to minimize friction for the end user. “When the friction goes down, your efficacy automatically goes up,” Patel said.
Keep this page bookmarked for articles and videos from the event, and follow us on Twitter @BizTechMagazine and the official conference Twitter feed, @RSAConference.