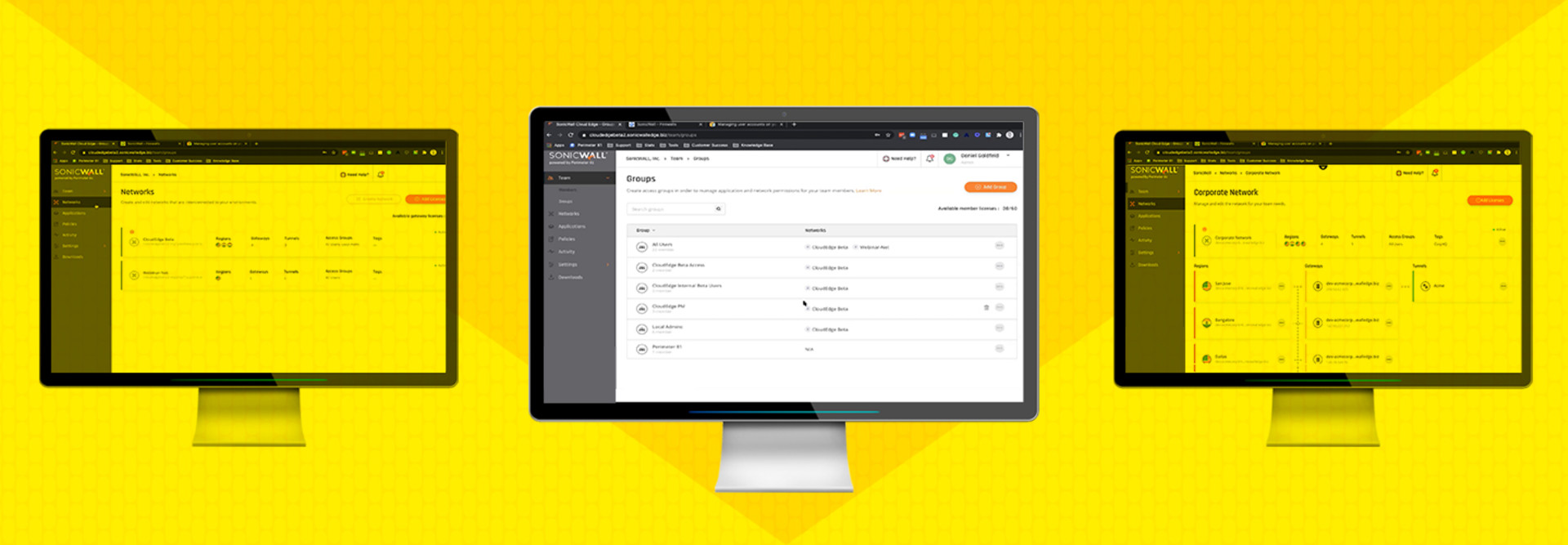
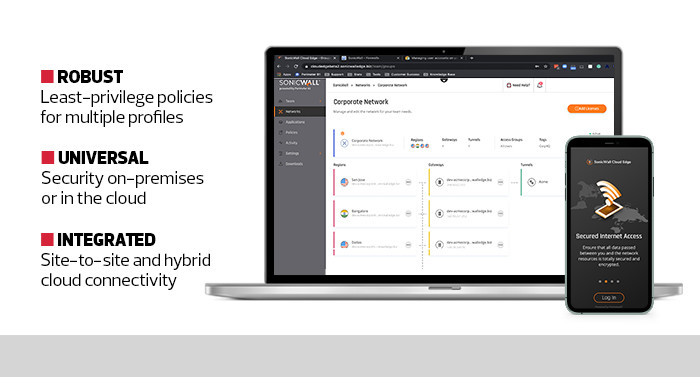
SonicWall Cloud Edge Secure Access not only securely connects remote or onsite users to corporate resources on any cloud platform or multiple cloud platforms, it also further prevents even authorized users from accessing parts of the network where they have no legitimate business.
This prevents the occasional disgruntled employee from making mischief. More important, it eliminates one of the biggest challenges in cloud security: malicious lateral movement by threat actors who do gain access. So, even if a hacker compromises a valid user’s identity, that actor will have severely restricted permissions by default and be under constant scrutiny by the platform.
The platform knows things like where users are accessing the network from, the devices they are using, their historical access records, their authorization levels and the kinds of activity they are attempting to perform. Cloud Edge even leverages microsegmentation to thwart unauthorized lateral movement across clouds.
Cloud Edge also employs least-privilege protocols. That means awarded permissions are never permanent, and users must be reauthenticated by the platform even when performing previously authorized tasks. This is handled automatically by Cloud Edge and applies to every user interaction.
A final impressive aspect of Cloud Edge is the administration interface. Navigating the complex nature of zero-trust networking protection was relatively easy in testing, with most features handled automatically by the platform with minimal user direction needed.
As businesses move more workloads into more clouds, securing those workloads is increasingly complex. SonicWall delivers the peace of mind that cloud-first organizations need.