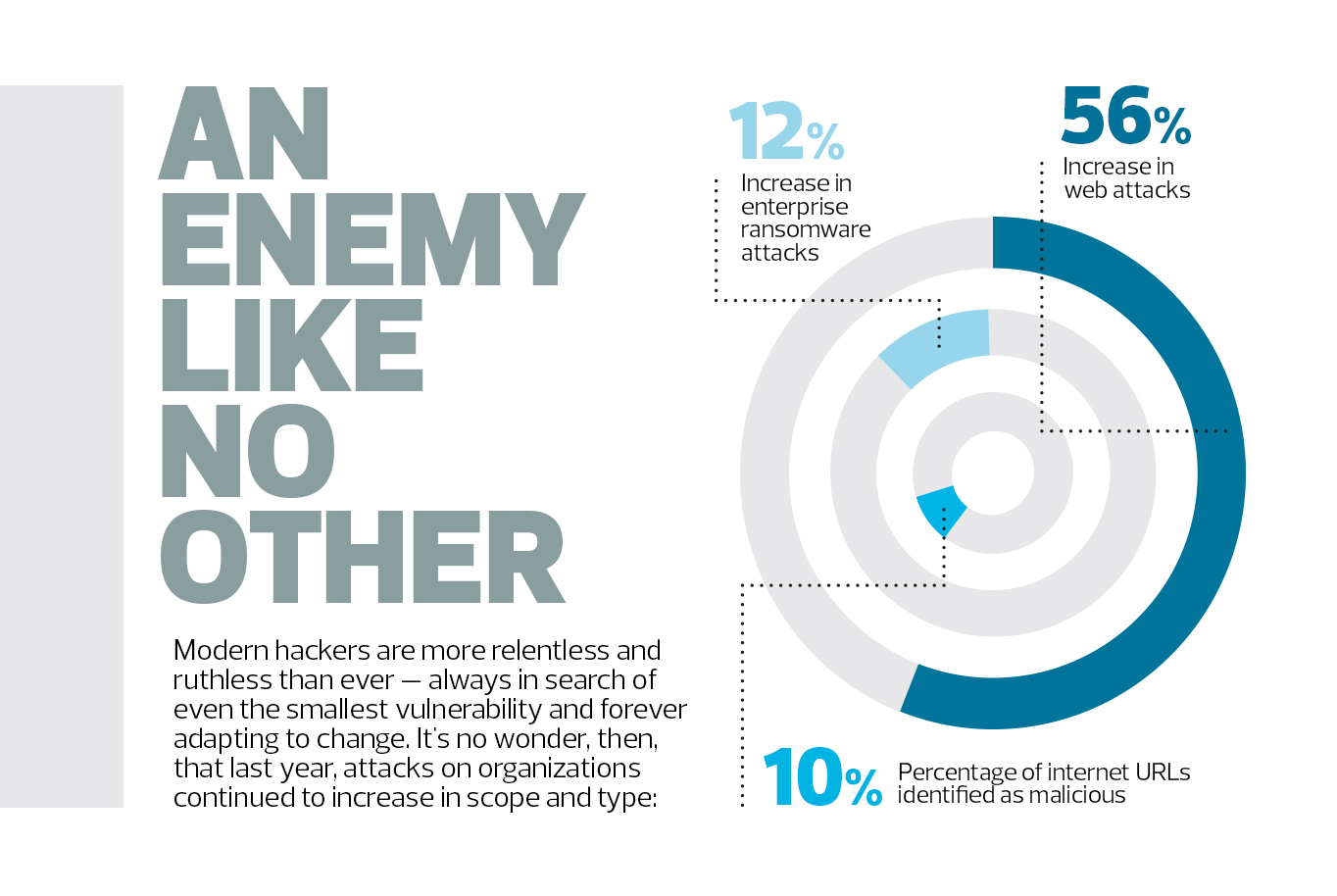
When it comes to cyberthreats, the numbers are staggering. More than 350,000 new malware variants are detected by the AV-TEST Institute every day. One in 10 internet URLs hosts malicious content, according to Symantec. And the Ponemon Institute notes that more than a third of successful attacks are the result of zero-day exploits, which take advantage of previously unknown software vulnerabilities.
In the face of attackers’ shifting tactics, firewalls, anti-virus software and intrusion detection systems are not enough. That’s why companies like SE2 are turning to threat intelligence services as part of a comprehensive cyberdefense posture.
Based in Topeka, Kan., SE2 provides financial and administrative services for some of the largest insurers in the world. Because it deals with thousands of sensitive and highly regulated health records every day, it must be constantly on guard against critical threats, says Nathan Girard, the firm’s chief information security officer.
Threat Intel Flags Suspicious Payloads Early
SE2 uses Check Point Software’s SandBlast for threat emulation and inspection. When its Check Point firewall detects a suspicious payload entering the network, it quarantines the file and runs the code inside a sandbox — a virtual machine designed to emulate a desktop or server — to see how it behaves.
“Once that payload comes in, our firewalls will break it open, connect to Check Point’s cloud ecosystem and have the code analyzed,” he says. “For example, if the code is attempting to invoke a registry change or a privilege escalation, we’ll send that data to Check Point, and they’ll send back a risk calculation. We can then decide whether we want to block that file or accept it.”
 As many as 60 potential incidents are flagged in this manner every week and are then triaged by SE2’s security staff, says Girard.
As many as 60 potential incidents are flagged in this manner every week and are then triaged by SE2’s security staff, says Girard.
“Every company has incidents,” he says. “It’s all about finding indicators of compromise, running the kill chain and reducing the amount of time it takes to get those potential attacks out of your environment. I’d rather get a call and have someone say, ‘We found a threat and killed it, and 50 records were impacted instead of 5,000 or 5 million.’ The threat intel we get from Check Point and the other products in our ecosystem is absolutely critical because we can find those IOCs much faster now.”
How Threat Intelligence Provides A Competitive Advantage
Threat intelligence feeds can act as a force multiplier for small and medium-sized businesses, which often don’t have the resources to get a global view of cyberattacks on their own.
“Threat intel is useful for alerting companies to attacks that affect the same infrastructure and software the company is using, which may put them at heightened risk of a breach,” says David Monahan, managing research director for security and risk management at Enterprise Management Associates.
Threat intelligence is a key component of defense in depth at ACI Specialty Benefits, a global provider of employee assistance and student support programs, work-life benefits and corporate concierge services for thousands of companies worldwide. ACI deals with sensitive employee information and has been growing quickly via acquisitions, which means it’s constantly incorporating new staff, says Ryan Fay, CIO of the San Diego-based firm.
ACI needed a cloud-based security solution that was both scalable and easily automated, allowing its IT team to push out consistent policies and securely provision new devices without having to spend all of its time onboarding employees.
“It’s so easy to acquire a company and just forget about it and let it do its own thing,” Fay says. “The hard part is incorporating its core security functionality and understanding how its security model compares with ours.”
Palo Alto Networks’ Next-Generation Security Platform fit the bill perfectly: “Having a cloud-based solution helps us to be a little more security agnostic and then decide which areas we want to address.”
MORE FROM BIZTECH: Find out how businesses can simplify authentication procedures for their users.
Cloud-Based Malware Protection Simplifies Integration
Because it takes in more than 3 petabytes of employee data every month, ACI’s tech team also needed the ability to quickly identify and isolate new malware threats before they spread. While it looked at a variety of threat intelligence solutions, the company ultimately came back to Palo Alto Networks’ solution, WildFire Malware Analysis.
“When we went through our RFP process, we realized that Palo Alto had a cloud-based malware sandbox that’s fully integrated with the rest of its security suite,” he says. “We could push it into all of our next-gen firewalls, and when it detected anomalies it would send them to Palo Alto’s cloud service for analysis.”
Because ACI operates in markets around the globe, it also needed a solution that could adapt to different regulatory compliance schemes.
“I felt pretty confident that we could examine real-time traffic, get comprehensive reports on threats and vulnerabilities, and provide a security process that would pass audits,” says Fay. “It’s not a theoretical discussion any longer. If you’re not compliant with the General Data Protection Regulation, the financial loss can be huge.”
Using Palo Alto Networks’ security suite has paid off for ACI in other ways. It boosted network speeds by 40 percent and enabled the company to increase the number of client smartphones it could onboard by 50 percent. Now, instead of being merely a cost center, its advanced security capabilities have become a competitive advantage.
“To be a successful CIO, you need to have a technology roadmap that differentiates you from your competitors,” he says. “Customers can come to our site, put in their data and feel secure doing so. Because if they don’t, they’re going to go somewhere else.”






 As many as 60 potential incidents are flagged in this manner every week and are then triaged by SE2’s security staff, says Girard.
As many as 60 potential incidents are flagged in this manner every week and are then triaged by SE2’s security staff, says Girard.




