The Dangers of Inadequate Cybersecurity
For energy providers, the consequences of poor information security have moved from the cyber world to the real world.
In 2008 — before critical infrastructure cyberattacks were widespread — a devastating explosion destroyed a stretch of the Baku-Tbilisi-Ceyhan (BTC) oil pipeline in Turkey. Years later, investigators attributed the attack to cyberattackers who circumvented elaborate detection and protection systems, injecting malicious software into the pipeline’s control network.
Similar incidents have grown commonplace over the years. The Stuxnet worm ravaged an Iranian nuclear enrichment facility in 2010, while Chinese hacker groups, organized criminals and hacktivists have made numerous attempts to access or harm energy infrastructure.
Equally daunting, such cyberattacks present a clear danger for energy and utility workers, as well as the people and enterprises that depend on reliable power.
Check out the data points below for a clear picture of the threat landscape.
1. What Is the Cost of Data Breaches in the Energy and Utility Industries?
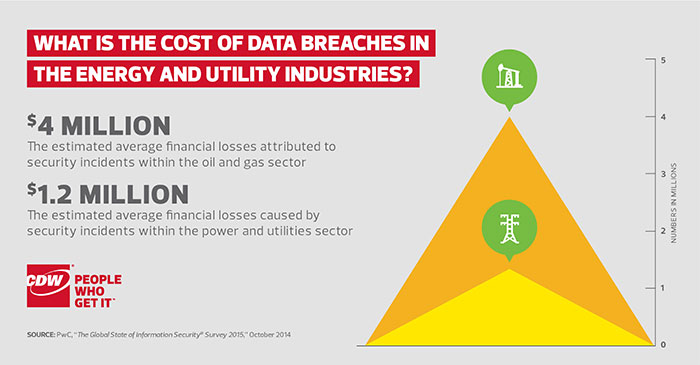
These figures may even understate the point, as many energy and utility companies didn’t include costs associated with reputational damage, legal defense fees or court settlements in their estimates.
2. Where Are Threats Originating?
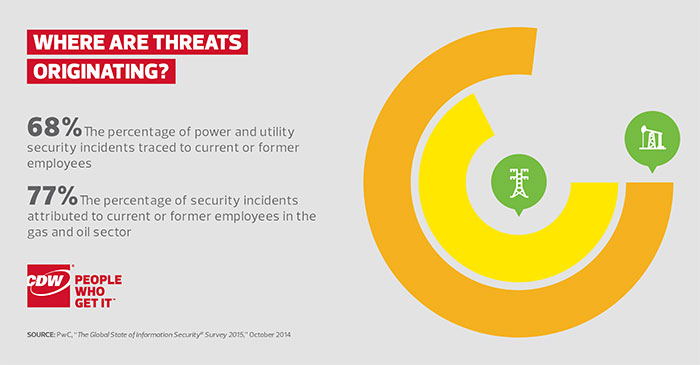
Insider abuse is a substantial problem for energy providers, highlighting the need for identity management tools, multifactor authentication and other safeguards.
3. How Sophisticated Are External Threats?

Considering that one zero-day exploit is enough to wreak havoc on a network, the Stuxnet worm posed an unprecedented threat that security executives will not soon forget.
4. How Quickly Are Companies Identifying Attacks?

Far costlier than breaches caused by human error, malicious attacks need to be identified and contained as soon as possible, yet a significant lag time remains.









