Be Proactive with Microsoft's Baseline Security Analyzer
One of the worst ways to find out about vulnerabilities or security holes is when it's too late. The bad guys employ a variety of tools to identify weaknesses to exploit PCs, so it's important to take proactive action to identify and mitigate those weaknesses before they do. The Microsoft Baseline Security Analyzer (MBSA) is a free tool from Microsoft that can keep IT admins a step ahead of would-be cyber attackers.
Microsoft Baseline Security Analyzer is a relatively simple tool provided for IT administrators at small to medium-size businesses. MBSA scans Windows PCs to detect common security misconfigurations, identify missing security updates and determine compliance with Microsoft security recommendations. MBSA generates a report with support and guidance to help remediate any security weaknesses discovered during the scan.
Scanning with MBSA
MBSA is a free download from Microsoft that is available in both x86 and 64-bit versions and is available in English, German, French and Japanese. After downloading it, double-click the MSI file to begin installation. After an initial screen is shown cautioning you to shut down all other applications before performing the installation is shown, select the destination folder where you want MBSA will reside (Figure 1).
Figure 1. Choose a destination folder for MBSA.
After the MBSA install is complete, click Start — All Programs — Microsoft Baseline Security Analyzer to start the program. MBSA requires elevated privileges, so you will most likely see a UAC (user account control) alert that you must accept before the program will start. The main MBSA console provides a brief blurb listing the versions of Windows that can be scanned using the tool, and explaining that MBSA needs Administrator privileges on each of the target systems in order to conduct the scan (Figure 2).
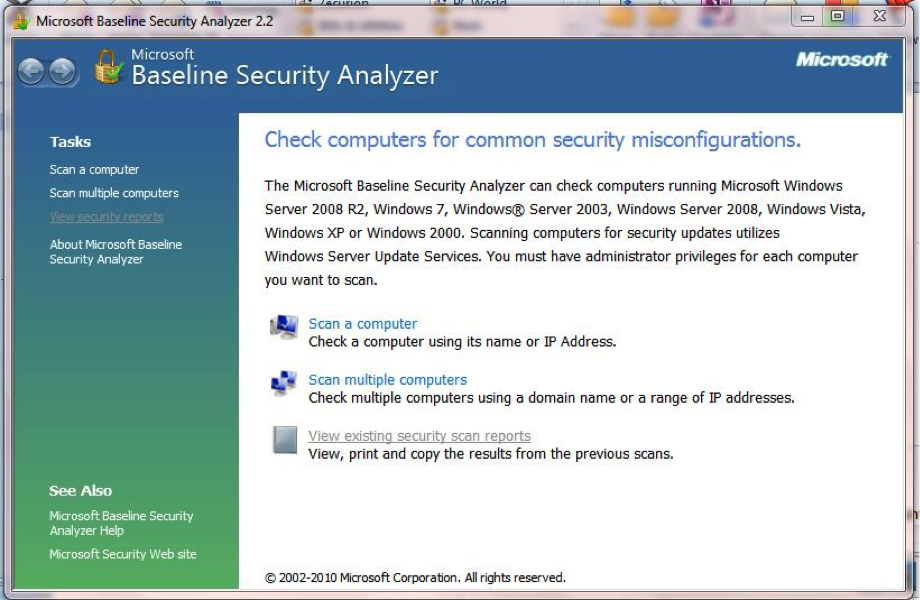
Figure 2. Determine system compatibility and choose between scanning a single computer or a range of computers.
As Figure 2 also shows, there are three options available from the MBSA console: Scan a Computer, Scan Multiple Computers and View Existing Security Scan Reports. As the names imply, the first choice allows a scan of a single target system, either by computer name or IP address, while the second scans multiple PCs, either by domain or by entering a range of IP addresses (Figure 3).
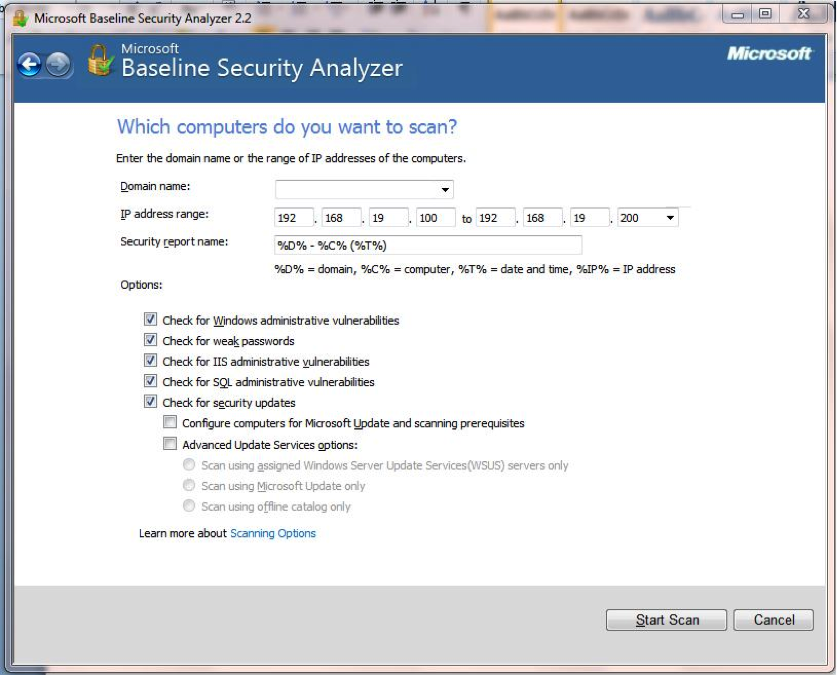
Figure 3. Give MBSA a domain or range of IP addresses to scan multiple PCs.
Keep in mind that MBSA relies on TCP ports 138 and 139 to perform vulnerability assessments on remote systems across the network. To conduct a security update scan on remote systems, MBSA requires a secure connection using DCOM through the Windows Firewall. For more on performing remote scans with MBSA, read "How can I scan a computer that is protected by a firewall?" in MBSA 2.0 Frequently Asked Questions on Microsoft TechNet.
When starting the MBSA scan, the obligatory progress bar appears, followed by a report summarizing the results of the scan. MBSA uses the universal green/yellow/red standard to show what the overall security state of the target system is based on the scan. A scan of my system came back with a yellow shield that is clearly labeled “Potential Risk (One or more non-critical checks failed)” (Figure 4).
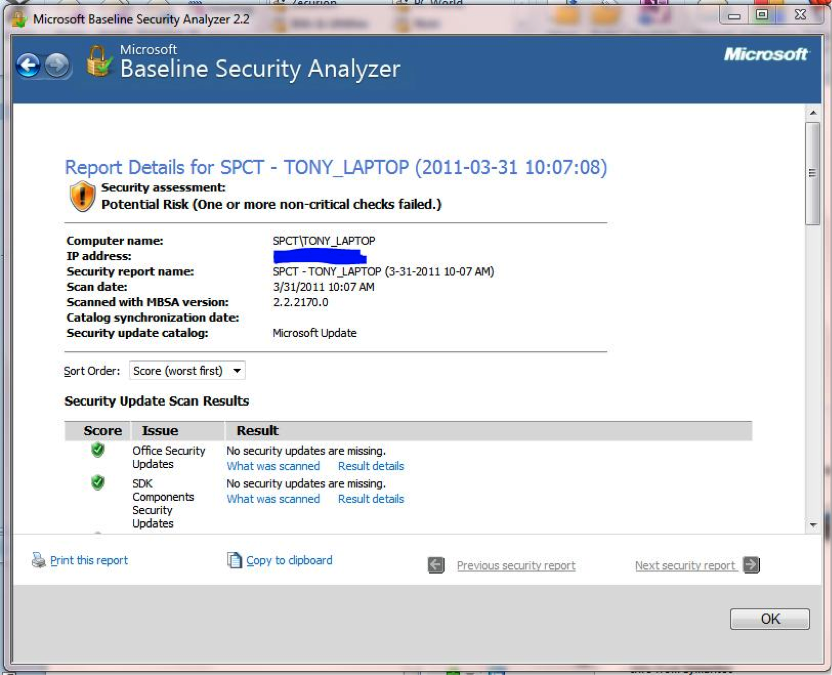
Figure 4. The yellow shield indicates that issues were found, but are not critical.
While scrolling through the report, the results of the various checks and tests are also labeled with green, yellow or red shields, or with a blue circle with a letter “I” to indicate an informational entry. Each result has a link showing what was scanned and another link to dig deeper into the results of that particular test. Tests that have results that need attention or remediation also have a link labeled “How to correct this” that provides additional guidance and recommended steps to resolve the issue (Figure 5).
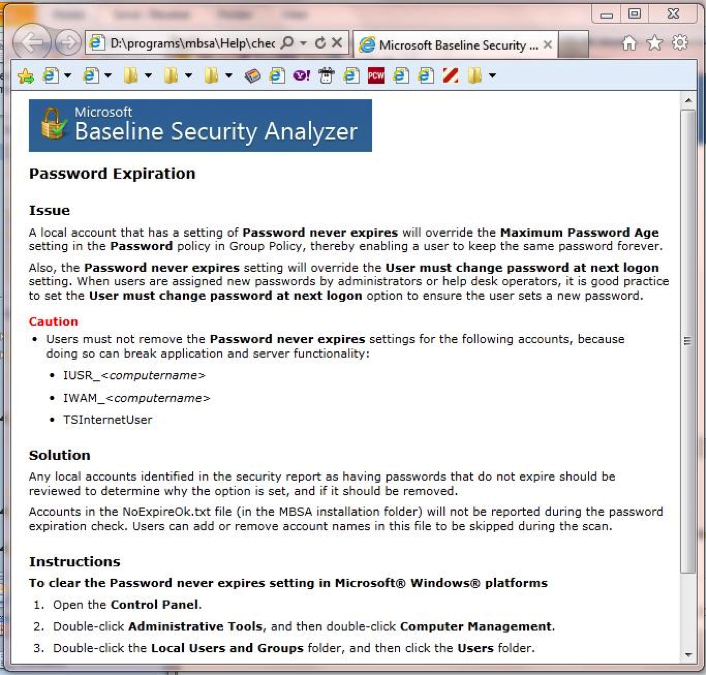
Figure 5. Microsoft provides guidance for resolving issues that are found during the MBSA scan.
Command-Line Control
The graphical interface version of MBSA — MBSA.EXE — is fine for most scanning purposes, but the command line tool — MBSACLI.EXE — provides more options and greater flexibility for IT admins. The command line tool can be used to conduct scans within a script and includes a variety of command switches to customize how the tool runs and what it scans.
/NVC — instructs MBSA to not attempt to connect to the Internet to check for an updated version of the MBSA scan tool.
/QP — instructs MBSA to not show scan progress.
/QT — instructs MBSA to not display the completed scan report immediately after a scan is completed.
/U — specifies the user name of an administrator-level user on the target computer(s).
/P — specifies the password of an administrator-level user on the target computer(s).
/RD — specifies an alternate location for the completed scan report.
For a complete list of the MBSACLI command line switches, open a command prompt from the folder where the MBSA files are installed, and type “MBSACLI.EXE /?”.
Legacy Support
MBSA can scan a variety of Microsoft operating systems and platforms, but older products that are not fully supported by Microsoft are not included. Organizations that need to be able to scan legacy platforms and products like the ones listed below can use Shavlik NetChk Limited, a free companion tool for MBSA from Shavlik Technologies. Shavlik NetChk Limited augments MBSA to scan the following:
- Office 2000
- ISA Server 2000
- FrontPage Server Extensions 2000/2002
- Visual Studio .Net 2002/2003
- SQL Server 7.0/2000
- Other products not included in Microsoft Update's supported product list
Shavlik Technologies is an independent third-party, not connected with Microsoft in any way. But, because MBSA is built on Shavlik's HFNetChk, the company is in a unique position to provide additional support to extend the functionality of MBSA.
Not a Silver Bullet
MBSA fills a role to help assess and remediate security concerns specific to Microsoft operating systems and software, but the tool is Microsoft-centric by definition and it isn't flawless, even at performing its designated role.
Microsoft security bulletins often contain work-arounds or manual fixes rather than patches to install. MBSA checks the Windows registry for keys to validate whether a certain patch has or has not been installed, but it does not have a mechanism for determining if these work-arounds have been applied. MBSA will report tests related to these security bulletins as yellow to signify that it was unable to determine whether the work-around was applied.
MBSA is also unable to tell whether there are additional layers of defense mitigating the threat and reducing the system's exposure to risk. Again, the check is Microsoft-centric, so it basically identifies whether the appropriate patches or work-arounds that Microsoft has delivered have been applied.
There are also discrepancies at times between MBSA scan results and the information displayed by Windows Update. For example, if patches are applied for security bulletins that have subsequently been updated, MBSA will flag those because it checks to make sure the most current updates are applied.
But Windows Update might not indicate that the updated patch needs to be applied because it is examining more specific elements of the system to determine if the changes made in the update have any impact.
Those minor issues aside, the Microsoft Baseline Security Analyzer is a great tool for proactively identifying and resolving security issues in an organization. Even better, the tool is provided for free from Microsoft, so the price is right, and there’s nothing to lose.








