Security Planning for Office 2010 Deployment
Deploying software to end-user computers in a business environment takes careful planning to ensure success. One essential part of the planning process is making sure that deployed applications comply with all company security policies. Many businesses have some version of Microsoft Office deployed; if yours is among them and you’re considering upgrading to Office 2010, then you need to ensure the deployment is configured to meet your organization's security needs.
Microsoft's Security Compliance Manager (SCM) has recently been updated to include settings for ensuring that Office 2010 applications are deployed in a configuration that aligns with the security requirements of your end user’s computing environment.
SCM is a solution accelerator (a tool and collection of best practices) that allows centralized management of the security of Microsoft Windows clients and server operating systems and applications, such as Microsoft Office, across an organization. SCM can help you create and customize security baselines and then deploy these as Group Policy settings to ensure the security configuration of your infrastructure is how it needs to be.
A security baseline is a collection of Group Policy settings that define the default security configuration of a Windows operating system or end-user software such as Microsoft Office. SCM includes pre-configured security baselines for different versions of Windows and Office that can satisfy the security needs of two types of organizations.
Enterprise Client (EC) baselines are designed to accommodate organizations that have typical security needs, while Specialized Security Limited Functionality (SSLF) baselines are designed for high-security environments where security is more important than functionality.
Each type of baseline comes in two forms: one designed to secure the configuration of end-user computers and one for securing the capabilities of the end-user accounts themselves. This ties to standard Group Policy format, which includes separate sets of policy settings for securing computers and users. These pre-defined baselines can also be customized to meet the particular security needs of different organizations.
Installing and Configuring the SCM
Once you've downloaded the SCM, you can install it on an administrator’s workstation in your domain. Installing the SCM is straightforward, but be sure to select the checkbox to automatically check for updates to ensure the latest baselines are downloaded for the tool (see Figure 1).
Figure 1
During installation, SCM downloads and installs the SQL Server Express Edition and creates a database instance used for storing pre-defined and user-created baselines. Once installation is complete, a dialog appears prompting you to download the baselines available for the tool (see Figure 2).
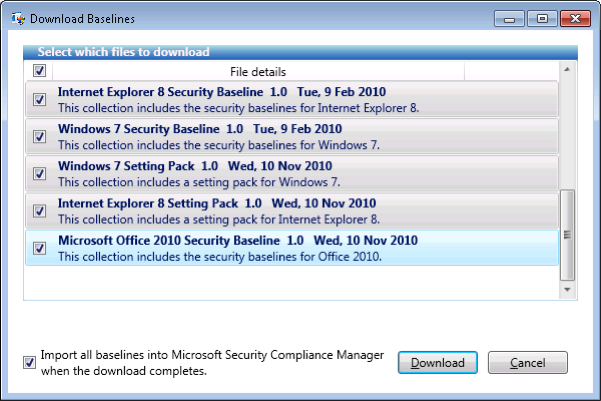
Figure 2
After clicking Download, you must respond to a series of security prompts to download the necessary package files for the baselines, after which you'll be presented with a summary of the package files that will be imported into the SCM (see Figure 3).
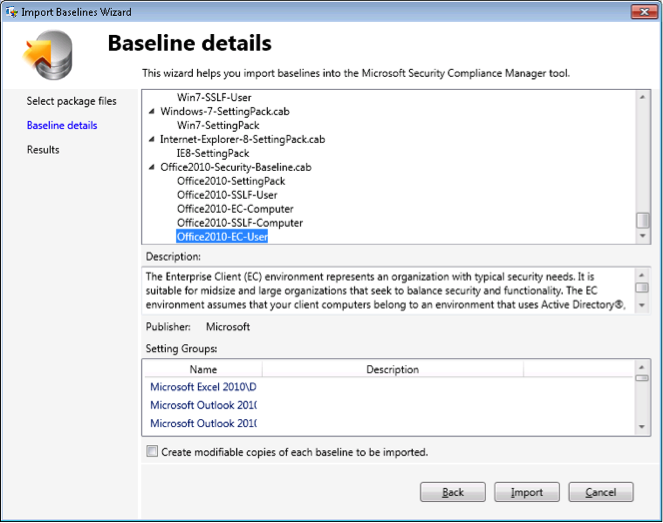
Figure 3
If you want to modify any of the predefined baselines, select the checkbox to create modifiable copies of each baseline to be imported.
Managing Office 2010 Security Using the SCM
Once updated baselines have been downloaded and imported, you can use the SCM to explore the different settings in each predefined baseline. Figure 4 shows the SCM console with default baselines for Office 2010 applications displayed in the left tree pane of the console.
The Enterprise Client baseline for Office 2010 users is currently selected, and middle pane shows the various security settings included in the baseline. These settings are grouped together based on similar functionality; for example, the settings for the Office 2010 Trust Center are currently selected in the Settings tab, while the individual settings in this group are displayed on the right with the Disable All Application Add-Ons for Word 2010 highlighted.
The Description tab shown at the bottom explains how this particular setting can be used to help secure Word 2010 functionality, while the Threats & Countermeasures tab provides more details about the vulnerability and its potential impact if exploited.
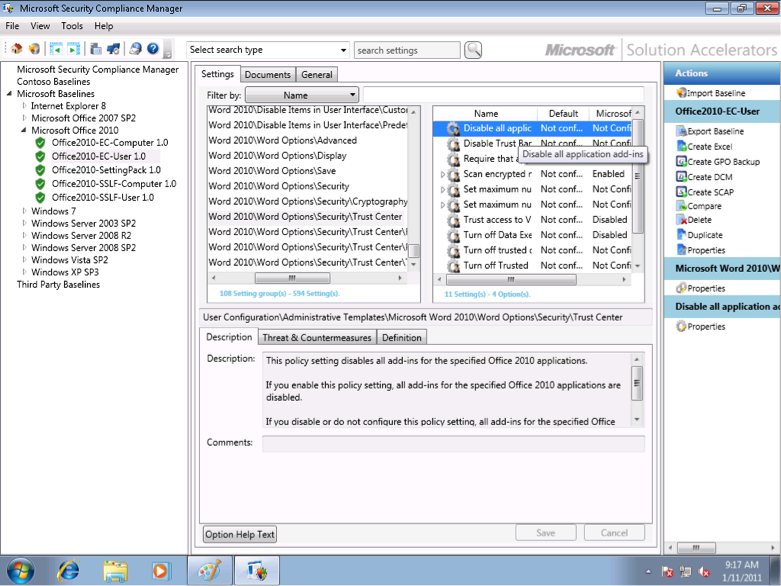
Figure 4
To use a pre-defined baseline like the Office2010-EC-User baseline in your environment, begin by making a duplicate copy because the predefined version is read-only. To do this, right-click on the pre-defined baseline in the left tree pane and select Customize and then Duplicate. An editable copy of the baseline will be created and assigned a default name and will be displayed under the publisher name used to identify your organization, which was specified during installation of SCM (see Figure 5).
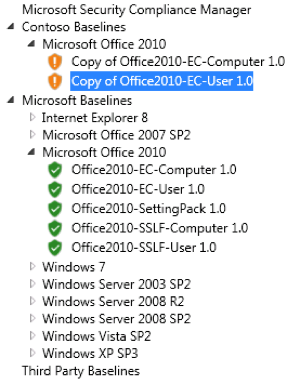
Figure 5
Then, configure the settings in your custom baseline by selecting each setting on the Settings tab in the middle pane of the SCM and configuring the setting using the Definition tab at the bottom. Figure 6 shows the same Word 2010 security setting described previously (Disable All Application Add-Ons), which has now been enabled within the custom baseline.
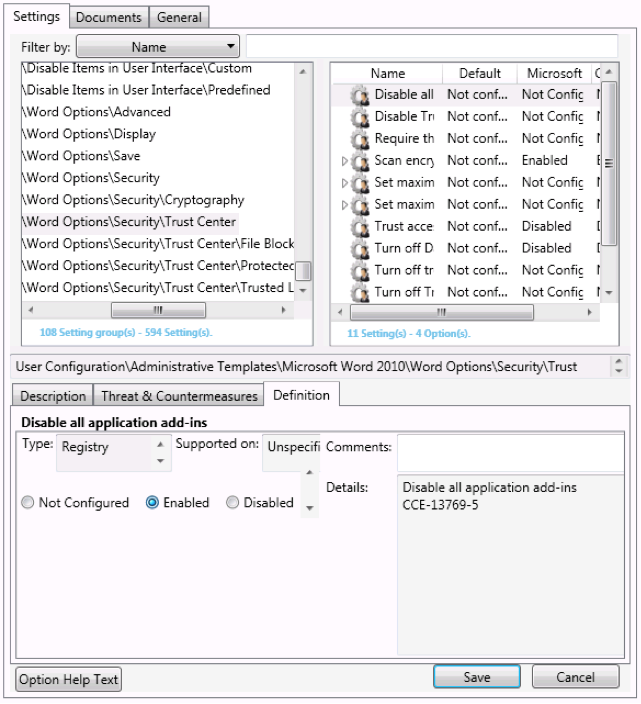
Figure 6
Once the setting is appropriately configured, click Save to apply the changes to your custom baseline. And once you've configured all the settings in your custom baseline in a way that is appropriate to your environment, export the baseline in a format that can be imported into a Group Policy Object (GPO) by right-clicking on the baseline and selecting Create, followed by GPO Backup. This will notify you to perform your own testing of the baseline to ensure it's appropriate for your environment (see Figure 7).
Figure 7
The result of performing the above export action on your custom baseline is a folder identified by a GUID, or globally unique identifier (see Figure 8).
Figure 8
You can then use the Group Policy Management Console (GPMC) to import your custom baseline settings into a new blank GPO and then apply the GPO to organizational units containing user or computers accounts in the usual manner. For more information about how to use the SCM, see the Getting Started guide in the TechNet Wiki.








