Patching known vulnerabilities has always been — and always will be — a foundational requirement for cybersecurity. But new data from SonicWall suggests that financial services organizations must be far more targeted and risk aware in how they approach patch management, while also investing in a layered cybersecurity strategy designed to withstand real-world exploitation.
In its 2025 Threat Brief, SonicWall reports that more than 6.9 million threats targeting Microsoft vulnerabilities were blocked by SonicWall firewalls in 2024 — a 110% increase year over year. For banks, credit unions, insurers and fintechs that rely heavily on Microsoft platforms to support mission-critical operations, this surge highlights an escalating threat environment with direct implications for customer trust, regulatory compliance and operational continuity.
However, the most commonly patched vulnerabilities weren’t always the ones attackers exploited most often. Remote code execution flaws represented 40% of vulnerabilities but accounted for only 19% of real-world exploits. Meanwhile, elevation of privilege vulnerabilities — which often operate quietly and evade traditional controls — made up 38% of actual attacks.
“With over 1,000 vulnerabilities patched and millions of associated threats blocked, one thing is clear: Patching alone isn’t enough,” says Douglas McKee, executive director of threat research at SonicWall. “Attackers are moving faster than ever to exploit the paths that provide the most rewards and least resistance.”
Click the banner below for deeper insight into modern cyber resilience.

The Most Common Vulnerabilities Aren’t the Most Exploited
One of the clearest lessons from SonicWall’s data is that volume alone can no longer drive patching priorities — particularly in environments where uptime, transaction integrity and data protection are paramount.
Security feature bypass techniques accounted for just 8% of known vulnerabilities, yet they were responsible for 29% of observed exploits. These methods allow attackers to disable safeguards, evade monitoring or move laterally — often without triggering immediate alerts.
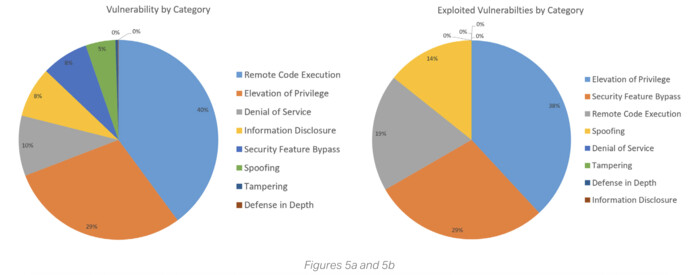
For financial institutions, where attackers frequently seek to escalate privileges to access sensitive systems or customer data, these techniques pose outsized risk. As a result, IT and security teams must prioritize patching and mitigation strategies based not just on the volume of common vulnerabilities and exposures, but on how adversaries behave in the wild.
Vulnerability Severity Isn’t Always What It Seems
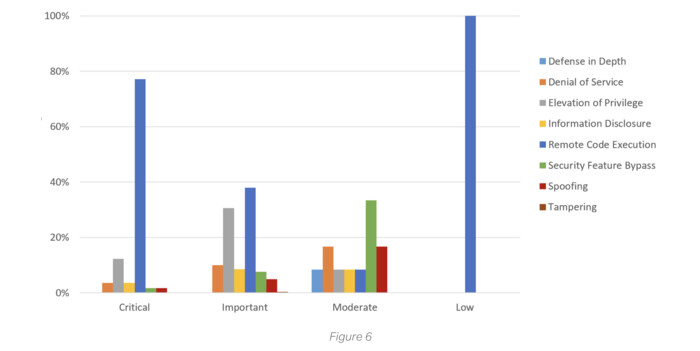
By the numbers, remote code execution vulnerabilities dominated Microsoft’s 2024 landscape. They accounted for 77% of the most critical vulnerabilities.
Yet severity scores didn’t always translate into exploitation frequency. Security feature bypass flaws, while less common and often rated lower in severity, were frequently leveraged to escalate access or disable controls — turning moderate vulnerabilities into incidents with severe consequences.
SonicWall also noted that Microsoft labeled 123 vulnerabilities as “Exploitation More Likely” in 2024, but only 10 appeared in the Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities Catalog. Two vulnerabilities labeled “Exploitation Less Likely” ultimately made the list.
Layered, Proactive Defenses Are Now Mandatory
Microsoft’s 2024 vulnerability landscape reflected complexity and volatility rather than sheer volume. While patching remains essential, determining how to prioritize patches has become far more nuanced.
“Organizations need a smarter, faster approach, one that blends real-time detection and response with layered defenses across every attack surface,” McKee says. He highlighted the following priorities:
- Identifying sophisticated privilege escalation attempts
- Neutralizing malware hidden in Microsoft Office documents
- Blocking exploits before they ever reach users
- Maintaining integrated protections across endpoints, email and networks
For financial services organizations, these capabilities directly support regulatory expectations, fraud prevention and operational resilience.
“Organizations that invest in coordinated, intelligence-driven security aren’t just keeping pace with threats — they’re staying ahead of them,” McKee says. “That can often be the difference.”
Supatman/Getty Images












