VMworld 2017: AppDefense Aims to Flip the Current Security Model on Its Head
Application security is about to be turned upside down, at least in VMware’s mind.
The cloud and virtualization company on Monday released AppDefense, its new security service, during the VMworld 2017 conference in Las Vegas. The solution leverages virtual infrastructure to monitor applications, check that they are running as intended and then respond as necessary if they are not.
VMware argues that the service “can significantly reduce the attack surface, making threat identification and response more efficient, and creating a more agile DevOps-friendly model for security.”
Gartner expects worldwide spending on information security products and services to reach $86 billion in 2017, which would be an increase of 7 percent over 2016. Yet VMware CEO Pat Gelsinger said during a keynote presentation that the cost of data breaches continues to grow, and grow rapidly.
“Fundamentally, we, the tech industry, have failed you, the customer,” he said. “It is simply too hard, too complex, and breaches are growing far too fast. We need a new approach.”
VMware’s approach combines three key elements: infrastructure that is secure by design, with security services becoming native capabilities of the infrastructure itself; partnerships with key security players, such as Palo Alto Networks, SecureWorks and Symantec; and a return to the basics of cyberhygiene, including microsegmentation of networks, encryption, multifactor authentication and patching.
AppDefense uses the compute layer of IT infrastructure for security. Most of cybersecurity, Gelsinger said, is about “chasing bad,” and trying to find a piece of malicious software among millions of processes and bits of data.
“That is really hard,” Gelsinger said. “Can’t we think about doing that a different way?” AppDefense focuses on “ensuring good” and keeping applications that run in the cloud and virtual environments safe.
“Chasing bad is like a needle in a haystack: There’s a whole lot of hay to crawl through,” Gelsinger said. “Ensuring good is getting rid of most of the hay and just having a few straws to go look at.” The approach VMware is taking is “flipping the security model on its head,” he said.
An Intent-Based Approach to Security
The AppDefense model is based on the idea of “least privilege” — that applications should have access to the resources and data they need, but nothing more.
“AppDefense delivers an intent-based security model that focuses on what the applications should do — the known good — rather than what the attackers do — the known bad,” said Tom Corn, VMware’s senior vice president of security products. “We believe it will do for compute what VMware NSX and microsegmentation did for the network: enable least-privilege environments for critical applications.”
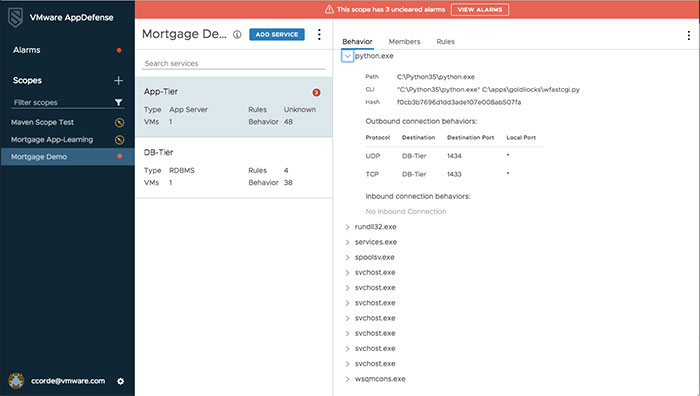
VMware's AppDefense service. Photo credit: VMware
VMware argues that AppDefense is in a unique position to see rich application context and can leverage the hypervisor to create a protected zone from which to store an app’s intended state and monitor runtime behavior. AppDefense also leverages VMware’s vSphere and NSX solutions to automate and orchestrate a response.
The service has three key elements or phases:
- In the “capture” phase, the service sees which applications and virtual machines (VMs) are running in a cloud or virtualized environment and which apps have been provisioned to which virtual machines. The service then “prevalidates” as many of the expected app behaviors as it can. Using machine learning, the service then determines the intent of the app and develops a “manifest” that shows what the app is supposed to look and behave like, Corn told reporters. These manifests will be maintained even as apps are updated and patched.
- The second phase is the “detect” phase, in which the service uses virtualization to construct a protected zone for storing the manifests for each VM. The service also monitors, in real time, what is running and compares it with the manifest. “It’s as simple as that,” Corn said. If an attacker starts manipulating the operating system kernel or processes, it creates a signal for the service to respond.
- The third phase is the “response” phase, which leverages the fact that in a software-defined data center, everything can be automated, Corn said. AppDefense has a library of incident response routines, including suspending a VM, blocking it, quarantining it using NSX, or inserting full-packet capture. “So you have a range of response mechanisms” that a security operations center (SOC) would want to have, Corn said. An IT team can set up whatever policies they want in terms of incident response, including gaining more visibility.
Corn said VMware designed AppDefense to be simple so that even a small IT team could run it. “One of the most limiting resources security organizations have today is staff, particularly sophisticated staff,” he said. “It’s an incredibly simple system to operate.”
However, he said AppDefense does require the involvement of multiple groups on IT staff; Corn said that VMware has recommended that early adopters of the service involve their SOC, a security architect and a member of their application team in the deployment.
Read more articles and check out videos from BizTech coverage of VMworld 2017 here.









