What Is IoT’s New Security Threat? It’s Called Hajime.
Kaspersky Lab recently blogged about a mysterious bit of malware called “Hajime” that is specifically targeting Internet of Things devices. This worm has infected around 300,000 devices so far, with Vietnam, Iran and Brazil seeing the highest incidences of infections. It was first reported in October 2016 by the security research group (SRG) at Rapidity Networks.
The Goal Is Propagation
What makes this piece of malware interesting is that it does not contain any attack code. Its purpose, right now at least, appears only to be propagation.
Konstantin Zykov, senior security researcher at Kaspersky Lab, points out that this botnet has not been involved in any known attacks or malicious activity. This lack of activity runs counter to the recent history of infected IoT devices. They’ve been used in a number of attacks, such as the October 2016 Dyn distributed denial of service attack.
Most of these botnet attacks have a specific architecture — controlled through a centralized malware distribution server. That’s not the case for Hajime-infected devices.
Instead, they communicate via a decentralized peer-to-peer network. Security experts believe this decentralized approach to propagation is deliberate and makes it more difficult to take down the Hajime botnet.
Exploring the Mirai-Hajime Connection
The initial report by the SRG at Rapidity Networks notes an interesting connection between Hajime and the Mirai virus. Hajime closely resembles the reconnaissance and infection behaviors of the infamous Mirai, which has been very successful at infecting poorly secured IoT devices. The SRG suggests there might be some connection between the two.
The timeframe of when Hajime was activated in the wild likely overlapped with the public release date of the Mirai source code on Oct. 14, 2016. The SRG believes that the worm’s similarities to Mirai serve to mask its presence, leading security professionals and network administrators to dismiss it as a Mirai attack and not bother to more closely scrutinize its code.
But there appears to be more to the Hajime-Mirai connection than the SRG revealed. ExtremeTech reports that once Hajime infects a machine, it covers its tracks and hides itself within the file system. Then it blocks access to four ports that are specific targets of the Mirai attack and displays the following message every 10 minutes on the device’s access terminal:
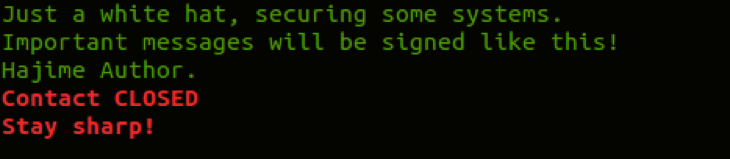
Could Hajime Actually Be a Savior?
Is there more to Hajime than meets the eye? By blocking ports 23, 7547, 555 and 5358 — the Mirai attack vectors — Hajime is actually making its infected devices more secure. Combined with the above terminal message, some experts believe that Hajime is the work of a white hat hacker vigilante seeking to secure IoT devices.
More interesting, Hajime’s design allows only its author to open a shell script on any infected machine in the botnet and add new capabilities, which are then distributed through the entire network.
And the author has noticed the attention his or her creation has garnered from researchers. The SRG’s initial report identifies bugs in the worm and provides signatures for detecting them. Since the report’s release, the bugs have been fixed. This task could only have been accomplished by the original author of the worm.
Skepticism About Hajime Remains
Despite the apparent good intentions of Hajime’s creator, the worm still worries security experts for a number of reasons.
Among them, it’s very uncommon for a malware author to directly take security research and improve a creation. This could set a pattern for more malicious-minded hackers doing the same thing — actively making their viruses even more harmful.
And there’s a good deal of skepticism among security teams as to the real intention of Hajime, with some suggesting that it could quickly be coded for nefarious purposes, given its peer-to-peer design. Time will tell if Hajime is really the beginning of a new era in malware design and distribution.









