What Small Businesses Need Know About ICANN’s Rollout of a New Root Zone KSK
October 11 will be a landmark day in the world of cybersecurity. For the first time in history, the Internet Corporation for Assigned Names and Numbers will change the master key used to sign secure Domain Name System records. ICANN officials created the current key at a secure data center in Virginia on June 16, 2010, and ICANN has not touched it since.
Although this change is significant to network security professionals, ICANN has said it should have minimal impact on users and organizations who own and operate domain names. The DNS key change process will take place over the course of a year to facilitate a smooth transition and avoid any adverse effect on internet operations. Just the same, IT leaders will want to monitor the transition and be vigilant for signs of malfunction.
How Does DNSSEC Help with Online Security?
DNS plays a critical role on the internet by acting as the internet’s directory service. The global network of DNS servers converts the human-friendly domain names familiar to users (such as www.biztechmagazine.com) to computer-friendly IP addresses (such as 54.243.103.249).
Thousands of servers around the world participate in the DNS network and perform two important functions. First, organizations that own domain names operate DNS servers that act as the authoritative source of answers for their domains. Second, network operators run DNS servers that answer questions on behalf of local users.
For example, imagine that a user on a business network wants to visit his or her bank’s website. The user opens a web browser and types in the domain name “acmebank.com.” At this point, the user’s computer contacts the DNS server on that user’s local network and asks for the IP address associated with the “acmebank.com” domain.
If the local server already knows the answer to that question, it immediately responds to the request. If the local server doesn’t know the answer, it contacts the DNS server at the bank and obtains the correct answer on behalf of the local user.
Most of the time, this system functions perfectly (and transparently), but there is a major security flaw in the design of DNS. If a malicious individual gains access to a local DNS server, he or she can insert false records on that server in what’s known as a cache poisoning attack. The fictitious user in our example might then receive false information about the location of the bank’s website and be redirected to a site set up by the attacker to conduct phishing attacks.
ICANN established the DNS Security Extensions to block these attacks by using digital signatures to validate records stored on DNS servers. When using DNSSEC, users can be confident that the records they receive were actually created by the domain owner. DNSSEC works by establishing a chain of trust from the top-level managers of DNS down to the domain owners managing individual DNS servers.
Making a New Master Key for DNS
ICANN’s planned change later this year will modify the Root Zone Key Signing Key for DNS. Think of this key as the master password for the entire DNS system. Just as with a normal password, it’s important to change the key periodically to ensure that it remains under the control of authorized individuals.
ICANN uses this key to sign “delegation signer” records that grant domain name registrars the authority to create their own signed DNS records.
Registrars then use this authority to grant domain name owners the authority to sign records for their own domains. The key protects these transactions all along the chain.
Fortunately, individual domain name owners shouldn’t be affected by this change.
Everything that is happening will take place at the highest levels of DNS, and it will be up to ICANN, domain name registrars and software vendors to make sure that the internet is ready for October’s master key rollover.
Even so, it’s a good idea for every company’s IT team to keep a watchful eye on the key transition process, looking for any unanticipated side effects or hiccups. ICANN has created a Root Zone Key Signing Key Rollover website that will provide updates and technical details on the progress of the change. If anything goes awry, information and action plans will be posted to the site.
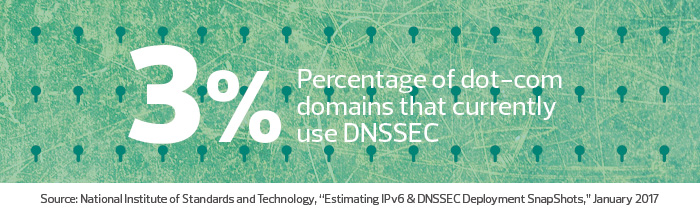
If all goes as planned, the change to the new key will take place quietly this October. While businesses don’t need to take any action to facilitate the change, it is a great time for domain name owners to take a look at DNSSEC and consider deploying this important security technology for their domain names if they have not done so.