Businesses Bring the Desktop and Mobile Worlds Together for Added Flexibility
The productivity benefits of mobility have become impossible to ignore. But some organizations have been reluctant to fully incorporate mobile devices into their operations, largely because of concerns about management and security. For many of these enterprises, mobile solutions remain fairly isolated from desktop workspaces and legacy applications.
But this isolation creates its own concerns. To address these issues, many enterprises are considering the deployment of end-user computing (EUC) solutions. Also called “digital workspaces” or “mobile workspaces,” these tools bring the desktop and mobile environments together, creating a seamless end-user experience that combines the enhanced productivity of mobility with many of the security and management advantages of traditional computing.
“Gone are the days when the IT department issues out a standard desktop PC and all the applications are going to stay behind your corporate firewall,” says Robert Young, research director for IT service management and client virtualization software at IDC. “How do you get this mix of applications — legacy apps, native mobile apps, Software-as-a-Service apps, web apps — to run across different hardware and keep the data secure? That’s hugely challenging. And one of the ways to do that is with a mobile workspace.”
 Workspace à la Carte
Workspace à la Carte
While several vendors offer integrated mobile workspace suites, enterprises can still mix and match products and capabilities in a way that best suits their needs. Reasons for taking this approach vary widely. Some organizations might not be able to afford an entire mobile workspace suite and opt instead to purchase individual products, while others may already have different mobile workspace solutions from various vendors in place.
However, Robert Young, research director for IT service management and client virtualization software at IDC, warns that this approach requires careful planning to succeed.
“There are some challenges with doing it piecemeal, but some folks may already be invested in Citrix XenApp or VMware Horizon Air or a particular EMM vendor, and they may not want to move off of those,” he says. “It’s something that has to be thought out really well: What does my existing environment look like? What tools do I already have? There’s a lot to think about.”
The Building Blocks of End-User Computing
Comprehensive end-user computing solutions share several common components or features: virtualization, enterprise mobility management (EMM) and identity and access management (IAM). These features, in turn, give organizations enhanced capabilities around data security and application delivery, and also provide benefits to end users, including more streamlined access to IT resources.
Virtualization: End-user computing solutions typically rely heavily on both desktop virtualization (which separates users’ desktop images from PC hardware) and application virtualization (which separates applications from the operating systems on which they are executed). Server virtualization is also often utilized to deliver these solutions as efficiently as possible.
Separating apps and desktop images from hardware is critical for delivering these resources to end users on all of their devices. Some EUC solutions make virtualized apps available via an enterprise app store. “There’s one corporate catalog where I can go and see the apps that I have access to and where I can request access to new apps,” says Kevin Strohmeyer, a senior product marketing director for VMware. “That’s an important step.”
Dan Cote, a product marketing director at Citrix, says that mobile workspace solutions simplify the enduser experience while still allowing IT staff to customize that experience based on user roles. “You don’t have to treat every user the same way. Some may need a virtual desktop that is just like their native environment. Others are just going to want the applications,” he says. “Your end users, whether they’re field reps or the CEO, they’re not all technologically literate, and the moment you try to introduce a tech solution that goes against what they’re accustomed to in their native work environment, that’s when things start breaking down.”

Source: Entrepreneur, “Survey Finds Mobile Devices Lure Us Into Working Longer, But No One Objects Much,” November 2014
Enterprise mobility management: EMM solutions take a holistic approach to mobility management, incorporating mobile device management (MDM), mobile application management and mobile content management. These tools allow organizations to institute policies and enroll devices in the management system; give users access to secure containers on their devices; encrypt communications; and allow users to securely access, store, update and distribute content via their mobile devices.
While vendors have their own separate EMM tools, these solutions go hand-in-hand with virtualization and identity and access management tools. When applications are virtualized instead of stored on user devices, for example, IT staff can instantly revoke access to those apps when a user leaves an organization, greatly simplifying mobility management.
“It’s instantaneous,” Cote says. “You don’t have to worry about getting that device back or uninstalling applications. Once the credentials go away, they have no access to anything that’s stored in the data center.”
Identity and access management: Identity and access management tools, which give users access only to the apps and information they need to do their jobs, do more than simply keep organizations safe. These solutions also simplify the end-user experience through single sign-on, allowing users to access appropriate IT resources without subjecting themselves to needlessly burdensome verification processes. This ease of use not only saves time, but it may also increase adoption of enterprise apps.
“Identity management is a big piece of the mobile workspace,” says Young. “You want to set the right policies so you can have single sign-on, access based on user role, even geofencing, and present the applications that users need. It simplifies things for IT, and it also gives a more consistent experience for end users.”
 EUC and BYOD
EUC and BYOD
Bring-your-own-device (BYOD) programs are attractive to both users and enterprises for a number of reasons. Users enjoy working with the devices that are the most familiar to them, and they appreciate not having to carry multiple devices for both personal and work use. Enterprises see both cost and productivity benefits, as BYOD initiatives boost efficiency with a minimal effect on IT budgets.
However, BYOD presents a number of challenges for organizations, including issues relating to the management and security of the devices and applications, as well as the privacy of users’ personal data on mobile devices. Organizations often struggle to support multiple device types and operating systems, and they have understandable concerns about sensitive data residing on users’ personal devices. At the same time, users bristle at mobile device management solutions that give companies access to their personal data.
Mobile workspace solutions pave the path to BYOD by allowing users to employ their personal devices to access enterprise apps and data, without requiring that these resources reside on the devices themselves.
“If you have employees coming in with a who-knows-what device, there are all sorts of infinite configurations,” says Dan Cote, a product marketing director at Citrix. “Having a virtual environment that will run on any of those BYOD devices ensures a consistency of experience, and you’re also securing the apps accessed by those devices.”
A Variety of End-User Computing Solutions
Several vendors offer bundled solution suites that incorporate virtualization, EMM and IAM into a single system. Among the most popular are:
VMware Workspace ONE: VMware’s mobile workspace suite brings together VMware AirWatch (an EMM solution) and VMware Identity Manager (an IAM tool), along with VMware Horizon Air, which is a cloud management program that delivers virtual desktops and customizes the user experience for different devices and operating systems.
While on-premises options are available (and the solution needs to connect to an on-premises Active Directory), Workspace ONE was designed to be delivered with a cloud-first mindset. Rather than enrolling their personal mobile devices in an MDM system in the traditional way, users can download the Workspace ONE app from the Apple App Store, Google Play or Microsoft Store, and then log in to gain access to applications based on the policies set for those apps. The suite is licensed on a per-user basis, either through annual cloud subscriptions or perpetual on-premises licenses.
VMware recommends the suite for numerous use cases, including organizations seeking to create an enterprise app store, better manage Microsoft Windows 10, accelerate Office 365 rollouts, or support bring-your-own-device programs. Strohmeyer also touts the suite’s benefits for deployments of corporate-owned mobile devices. Rather than engaging in a cumbersome device configuration process, he notes, organizations can simply give users access to the appropriate resources based on their role when they log in. “It’s a great out-of-box experience,” he says.
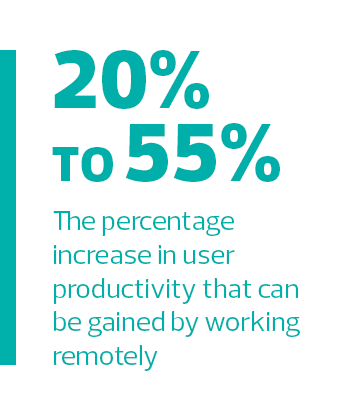
Source: Citrix, “2020 Technology Landscape,” April 2015
Citrix Workspace Suite: Citrix’s mobile workspace solution also brings together a number of standalone solutions from the vendor, including productivity apps; the virtualization tools XenApp and XenDesktop; the XenMobile EMM suite; ShareFile Enterprise, which is a secure enterprise file synchronization and sharing service; and the NetScaler Unified Gateway remote access solution.
Taken together, these tools give users access to the apps, data and desktops they need for work on any device, while also allowing IT staff to centrally manage access based on user roles. A user working from home on a personaliPad, for example, can use Citrix to access a desktop (fully optimized for mobile), access individual apps or launch a secure email client. The email client opens attachments via a built-in secure viewer — rather than downloading them to the device — preventing sensitive documents from being stored on tablets and smartphones that are vulnerable to loss and theft.
“The key reason people choose Citrix is around centralizing and securing your apps and data,” Cote says. “If you have a notebook, even with a virtual private network, there are still some issues and challenges. You’re downloading files, and if someone steals that notebook, now you have intellectual property that is out in the wild. In sectors like financial services and healthcare, you simply can’t afford to do that.”
Microsoft Enterprise Mobility Suite: Microsoft’s suite of solutions to support end-user computing includes Intune, a cloud-based tool that allows IT shops to manage devices and apps, and also to control access to data; Azure Active Directory Premium, which provides single sign-on capabilities and manages authentication for all devices and applications; and Azure Rights Management, which protects data on mobile devices. Microsoft offers this suite along with other tools that support mobile workspaces, including its Surface tablets and other mobile devices. Also included is Office 365, a cloud software suite that gives users access (across all of their devices) to document sharing, video messaging, online storage, email and popular Office apps such as Word and Excel.
The EMS solution not only manages Microsoft’s own applications, but also manages 2,500 cloud and mobile apps. Users are able to access managed apps without having to remember multiple user names and passwords, and Intune can push apps from the Google Play, Apple and Microsoft app stores to user devices. Alternatively, users can download apps from a self-service enterprise portal.
Networking for EUC
For a mobile workspace solution to thrive, an organization must optimize its networking infrastructure for mobility. Top networking vendors such as Aruba provide the switching and routing capabilities to support mobile deployments, as well as state-of-the-art 802.11ac Wave 2 wireless access points. They also offer network management and visibility solutions (such as AirWave Network Management), as well as identity and access management tools (such as ClearPass Network Access Control) and app and content management systems (such as Meridian Mobile App Platform).
Christian Gilby, director of product marketing for Aruba, says these networking tools allow organizations to create environments in which mobile workspaces can thrive. Some enterprises are using network visibility tools to help them optimize real estate, and others are using tools such as Aruba Clarity to proactively seek out connectivity problems and fix them before they affect users.
“From an infrastructure perspective, we’re seeing that shift, where wireless is now the primary or only connectivity to get onto the network,” Gilby says. “There’s more consumerization, with people bringing their own smartphones or notebooks. It’s a different workforce coming into play.”









