Kernel of Trust: New Mobile Security Features Improve End-Point Protection
If Verizon’s recent Data Breach Investigations Report is to be believed, then mobile devices have yet to be deluged by the dark forces of cyberattackers and their malware minions. According to Verizon’s research, only about 100 smartphones per week are infected, out of tens of millions of devices out there. That makes for a 0.68 percent infection rate, which is quite small.
But as app downloads become even more ubiquitous, and more high-value banking and payment services go mobile, it’s safe to say that this will be a growing area of attack in the near future. To get ahead of this looming threat, device manufacturers and suppliers are taking steps to improve security, focusing on locking down the hardware environment to better protect devices from both software-born and physical threats.
Crossing Over to the TrustZone
Semiconductor company AMD is one such manufacturer, having licensed market competitor ARM’s TrustZone technology to provide a hardware security platform for its recently launched Pro A-Series of processors, which will run on mobile devices.
“AMD is going after this new security focus with a real fervor,” says Rob Enderle, principal analyst at the Enderle Group. “TrustZone has an impressive set of features, offering a real contrast to Intel’s security efforts. You don’t see these new options available anyplace else. This will prove valuable in the market, especially with the government sector.”
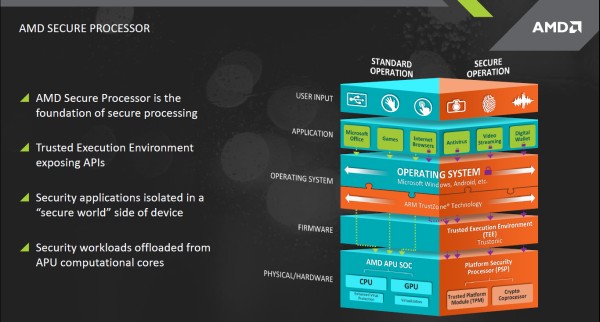
How exactly does TrustZone work? Diane Stapley, director of alliances at AMD, explains: “It’s a coprocessor that fits inside of our SoC [system on a chip], purely dedicated to security functions. It offloads and isolates from the rest of the CPU and GPU core complex. There’s industry standard APIs [application programming interfaces] that sit just above that, in a security kernel, in a trust zone – a trusted execution environment. Different applications that sit above can port using a standard SDK [software development kit] that’s offered in conjunction with our kernel partner. This provides the ability to run things strictly on that secure side of the device.”
TrustZone technology allows only approved software to run on its security-focused coprocessor. The chip isolates sensitive functions running on the devices (such as authentication systems tied to payment services) in a computing environment that hackers cannot break into. This arrangement with ARM provides AMD with a trusted security feature for its consumer-device-focused processors.
“TrustZone uses industry-standard APIs,” says Stapley. “You’re working on something that has an actual ARM processor in it. And you’re using a separate process that is isolated to do your work. It’s a very similar methodology across all the different products. ARM TrustZone has been very well adopted in the smartphone and tablet market to date.”
Enderle sees this addition to the Pro A-Series chips as a smart move. “AMD adopted TrustZone because it was going to be less expensive and require less effort than developing it themselves from scratch. The ARM architecture was the perfect fit for the job. They wanted something that’s intelligent, that looks at behavior instead of just running a script. This gives AMD that option. It’s a differentiator from Intel’s Atom chips. Most hackers will be formulating their attacks for Intel chips because they’re the market leader. These attacks won’t be successful with an AMD chip.”
An Eye for Eavesdroppers
Baking in an industry-standard technology opens up new horizons for additional root of trust security features that AMD is starting to integrate into its processors. One such opportunity comes via the company’s new partnership with advanced security products developer OptioLabs, which will integrate its PrivateEye technology into AMD’s Pro A-Series processors.
PrivateEye prevents visual eavesdropping of a device’s screen. It does this in a couple of ways. First, it blurs the device’s screen whenever the biometric-authorized user turns his or her attention elsewhere. And it can warn the user when an eavesdropper is detected nearby, then automatically blur the display when one is captured by the device’s camera.
“We’re leveraging the camera in the notebook or tablet,” explains Gregg Smith, CEO of OptioLabs, “and we’re providing continuous authentication using facial-recognition technology. The technology is constantly checking – typically about every 15 seconds – that the authorized user is actually looking at the computer and looking at the data on the screen. If someone happens to look over their shoulder, the camera captures that eavesdropper and fuzzes the screen.”
AMD’s use of TrustZone was key to its partnership with OptioLabs. “It will be a simple port over for us from our standard product to tie directly into the Pro series. The fundamental philosophy of our company is hardware-based security. Hardware-based security will beat software any day. The fact that AMD is providing that trusted root with TrustZone tying in with PrivateEye is another big check in the box for us. It now allows us to go into regulated markets and the government space.”
Blitzing the Chip
Another recently announced opportunity to help AMD secure that last two feet of the network is its partnership with ExactTrak. AMD will soon be embedding ExactTrak’s Security Guardian technology into the Pro Series processors. This technology, originally developed in a USB form factor, focuses on protecting data. Since it’s embedded in the chip, its features are in place before the OS boots up.
ExactTrak’s technology allows users to track the location of devices through the device’s battery, GPS, GSM and satellite functionality. Being able to track the location of the device allows the enterprise to set parameters as to when and where its data can be accessed. For example, access to data on the device might be set for working hours only and within a particular office building.
“We give enterprises, SMBs and consumers visibility of where their device is, visibility of what it is doing,” explains Norman Shaw, founder and CEO of ExactTrak. “And the various features can be turned on and off. The GPS tracking feature, for example, can be set to turn off after you leave your work building. The enterprise doesn’t have any interest in or need to know what nightclub you’re going to. It’s a privacy issue too.”
ExactTrak’s technology is sold as a service. A cloud-based management console (hosted by a global service provider) is used to send instructions and parameters to the chip. This close scrutiny of the data on the device means that organizations can also monitor any actions taken with the device’s files. Adding, deleting, copying or printing – all of these actions are logged and available for review through the management console. And if the device is lost? First, the memory on the device can be remotely turned off, making the data inaccessible. The memory microchip can also be destroyed remotely.
“That gives people a big buzz, knowing they can blitz the memory chip,” Shaw says, laughing. “But behind all of that is a verifiable audit trail for compliance. This is vital in the enterprise space. That verifiable audit report will show a complete transaction history of how a robust mobile data security system is being implemented.”
ExactTrak was another company already using TrustZone before it partnered with AMD, making for an easier transition of the technology to AMD’s ecosystem. “We’re a TrustZone developer,” says Shaw. “The AMD Pro series now gives us the opportunity to do the whole thing in line.”