Find the Holes in Your Network with Nessus
Networks are being compromised and sensitive data exposed almost daily. Thanks to the recent exploits of groups like Anonymous and LulzSec, it is glaringly apparent that hacking into the organizations of most networks is mere child's play. Would your network withstand an attack? How do you know?
It is time to be more proactive about securing your network by employing a tool such as the Nessus Scanner from Tenable Security to identify weaknesses before the bad guys do. Plain and simple, the bad guys employ tools and techniques to find holes in target networks, so there is no reason that you can't use the same tools and techniques to beat them to the punch and close the holes to protect your network.
Types of Scans
The Nessus Scanner can perform four basic types of scans to identify network vulnerabilities and weaknesses:
-
Passive scanning looks for systems and services that broadcast their presence across the network. A “passive” scan doesn't actively scan; it sits, listens and waits for the network data to come to it.
Attackers have a variety of tools available to perform passive scanning (also known as network sniffing) to compile a list of the active systems, applications and services advertising themselves. Nessus can conduct passive scans so companies can pre-emptively discover what an attacker might see, identify issues and take action to protect systems.
-
Active scanning is the opposite of passive scanning. Active scanning sends out packets to probe the network and can be used to find open ports and active systems that may not be broadcasting their presence.
Active scanning is intrusive and might be detected as suspicious activity, so attackers are less likely to employ active scanning tools. But, active scanning returns more comprehensive results, more quickly, than passive scanning.
-
Host scanning looks beyond the existence of the system — or its active services and open ports — and analyzes the security configuration of the system itself. Host-based assessments can probe the patch level and security configuration of the system to discover vulnerabilities and weaknesses.
-
Perimeter/cloud scanning allows you to truly see what external attackers see, from outside your network. Other types of scans are good for identifying and closing holes that an attacker might be able to exploit if they first gain access to your network, but conducting a web-based vulnerability scan of your perimeter provides valuable insight into how your network might be exposed or vulnerable from the public web.
Creating a Policy
Nessus Scanner and its downloadable plug-ins come with default policies, but it’s possible to create a scanning policy to emulate just about any imaginable scenario. You can determine virtually every aspect of the scan policy and be as passive or aggressively intrusive as you wish. Select the Policies tab in the Nessus Scanner client console, and click the button with the green plus-sign icon that says Add. There are four elements to configure for the Nessus policy: General, Credentials, Plugins and Preferences.
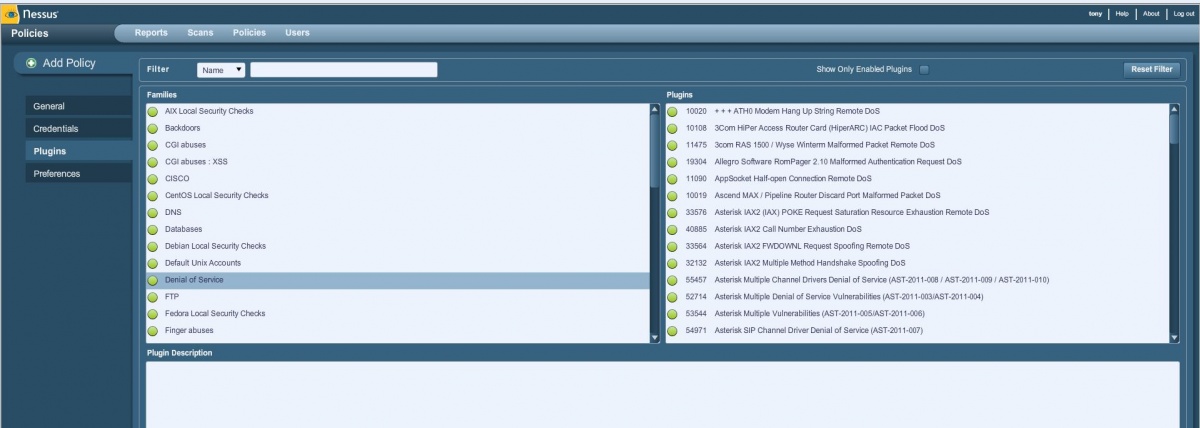
Figure 1: Choose which Nessus plug-ins to include in your scan policy.
You can create Nessus policies that include login credentials for Windows PCs, database settings or services such as FTP. But hopefully an external attacker won't actually have that information, so you don't need it if you are just trying to determine what systems or services are exposed to outside attack.
Start by giving the policy a name and setting the General configuration settings. When you are ready, click Next at the bottom right to move on to Credentials. Continue setting the policy configuration for each element and clicking Next to proceed. Once you configure the Preferences, click Submit to create the policy.
You can also import Nessus policies you already have, or that have been created by third parties, by clicking the button with the orange up-arrow icon that says Import.
Conducting a Scan with Nessus
To perform a scan, select the Scans tab on the Nessus Scanner client console. As with the Policies tab, start a new scan by clicking the button with the green plus sign and the word Add.
Give the scan a name that will help identify it later (perhaps the domain being scanned, or type of scan being conducted, combined with the date to make it unique). You can choose to either run the scan immediately or schedule it to run at a later time. This is helpful if you want to conduct a scan at night or on the weekend to ensure it doesn't impact productivity.
There is a drop-down list to select which policy to use for the scan. Any policies created or imported will appear here along with the default policies installed with Nessus. You can designate target systems to scan by IP address, IP range or host name. You can also import a list of scan targets from a file.
Once the selections are made, click the Launch Scan button at the bottom right.
Reviewing Reports
Once a scan is launched, it will appear on the list under the Reports tab. While it is running, the status is listed as Running. Once the scan is done, the status will change to Completed, and you can double-click the scan name to open the report and review the findings.
The report will show at a glance each scanned host, along with the total number of issues detected, a breakdown of High, Medium and Low priority issues, and the number of open ports detected. You can click on the different elements, such as the number of Medium priority issues, to drill down for more details.
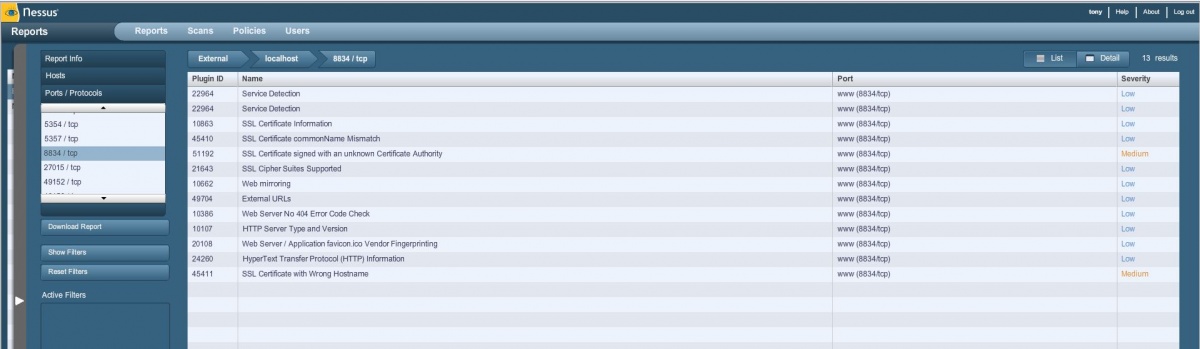
Figure 2: Click on elements of the report to drill down and review details.
Drilling down eventually leads to a detailed description of the issue, as well as a suggested solution to resolve the problem.
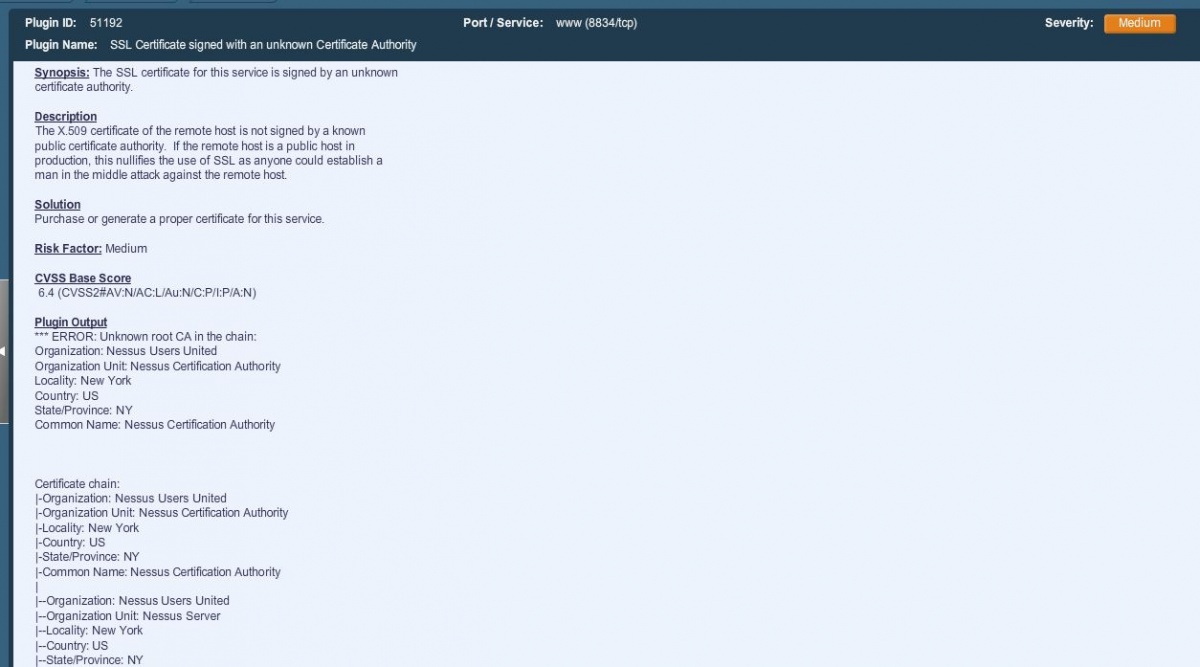
Be Prepared with Nessus
Nessus is a powerful tool for staying one step ahead of attackers. With the variety of plug-ins available, Nessus can also be used for quick self-audits against security standards and compliance mandates, such as Microsoft baseline recommendations, PCI-DSS and more.
The Nessus Scanner software itself can be downloaded for free. However, in order for the software to be of any use, you need the Nessus plug-ins, and that requires a subscription to the Nessus Professional Feed, which costs about $1,200 per year.
The cloud-based Nessus Perimeter Service is separate from the basic Nessus Scanner, and costs about $3,600 per year.








