Best Practices Analyzers Ease the Burden of Server Configuration and Management
Whether you’re deploying file servers, web servers, database servers or any other type of server in your environment, best practices can help steer you in the right direction for that server’s role. In IT terminology, best practices are guidelines IT workers can follow for planning, deploying, configuring or maintaining technology.
In the old days, best practices were published in the form of checklists that an IT worker could walk through when configuring a server. Necessary firewall ports opened? Check. Service accounts running with the proper privileges? Check. Resource records properly registered in the DNS servers? Check. And so on.
Unfortunately, there were several problems with this approach. First, IT workers needed to understand how to properly use the tools to perform all the steps on these lists. That meant being able to configure firewalls, rights and privileges, DNZ zones and more.
The reality is that IT workers can't always know everything about every feature of every server operating system or server application. To remedy this, organizations like Microsoft published best practices for their products that often went into great detail about how to implement every step.
But the more detailed the instructions, the greater the opportunity to introduce errors. IT workers are busy; they don't always have the time to read through a long list of complex configuration steps.
Instead of trying to understand each step, some IT workers shifted their brains into low-power mode and just blindly followed the instructions. If they missed something or misread a step, a network service or application might function unpredictably or not at all.
Enter the BPAs
To make the administrator's job easier, Microsoft created best practices analyzers, or BPAs, a few years ago. These free tools run on a server and verify whether the role or application was configured properly for the environment.
For example, the Exchange Best Practices Analyzer for Exchange 2007 collected information from Active Directory, the Windows registry, the IIS metabase, performance monitor and other sources. Once the data was collected, the BPA applied comprehensive best practice rules to the Exchange topology to identify any misconfiguration or possible problems.
The administrator could then use the BPA to generate a detailed report that included recommendations on how to fix any misconfiguration issues identified to achieve greater performance, scalability and uptime.
A number of these BPAs are available for download from the Microsoft Download Center. For example, the Microsoft SQL Server 2012 Best Practices Analyzer was released in April 2012 and is a must-have for those who plan on deploying SQL Server 2012 in their environment.
This BPA utilizes Windows PowerShell to perform its tasks, which means you can use it to scan both the local server and remote servers, provided the remote servers are configured for remote management. For more information about the SQL Server 2012 BPA, visit Microsoft's site.
Built-in BPAs
Starting with Windows Server 2008 R2, Microsoft made applying best practices even easier by building BPA functionality directly into the operating system. IT workers could use this built-in BPA functionality to scan and analyze roles such as Active Directory Domain Services, Internet Information Services, Remote Desktop Services, Hyper-V and many others. Find a full list of server roles that support BPA functionality on Windows Server 2008 R2 in the TechNet Library.
The New Server Manager
Windows Server 2012 takes BPAs a step further by integrating them directly into the new Server Manager console. Figure 1 shows the Best Practices Analyzer tile for the Active Directory Domain Services (AD DS) role in Server Manager on a Windows Server 2012 domain controller.
A filter has been applied so that only compliant results (configuration that adheres to best practices) are displayed. Each compliant result states the proper configuration setting and affirms that it has been configured properly on the server.
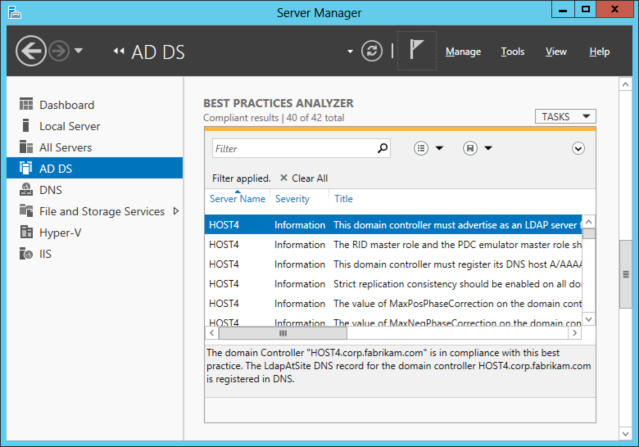
Figure 1: The AD DS role on this server complies with most best practices for this role.
Figure 2 shows a different BPA filter for the AD DS role on the same server. This filter displays the warnings or errors generated from the BPA scan. The results show two problems with the configuration of the domain controller.
The first says:
The PDC emulator master HOST4.corp.fabrikam.com in this forest should be configured to correctly synchronize time from a valid time source.
This issue is flagged as Error and should be corrected immediately. If the PDC emulator master in this forest is not configured to correctly synchronize time from a valid time source, it might use its internal clock for time synchronization.
If the PDC emulator master in this forest fails or otherwise becomes unavailable (and if you have not configured a reliable time server (GTIMESERV) in the forest root domain), other member computers and domain controllers in the forest will not be able to synchronize their time. Clicking the More Information link displayed at the bottom of Figure 2 opens a TechNet page with more information about this issue and how to fix it.
The second problem says:
All OUs in this domain should be protected from accidental deletion.
This issue is only flagged as a Warning because if all OUs in your Active Directory domains are not protected from accidental deletion, your Active Directory environment can experience disruptions from accidental bulk deletion of objects.
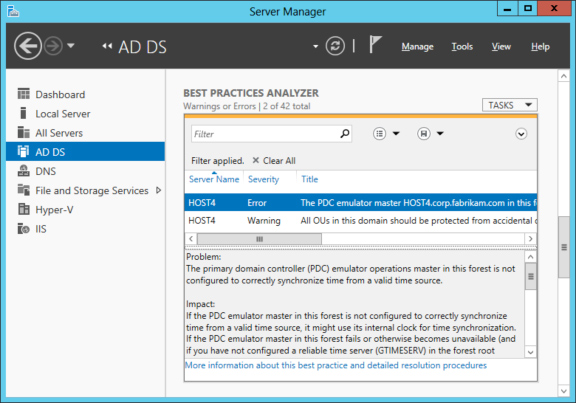
Figure 2: Errors shown in the BPA AD DS role.
After correcting these issues, you can rerun the BPA by clicking on the Tasks menu at the top right of the BPA tile.
By integrating BPA functionality into the Server Manager console of Windows Server 2012, Microsoft has made complying with best practices easier than ever. If IT workers use them wisely, there will be less to worry about in the server environment.








