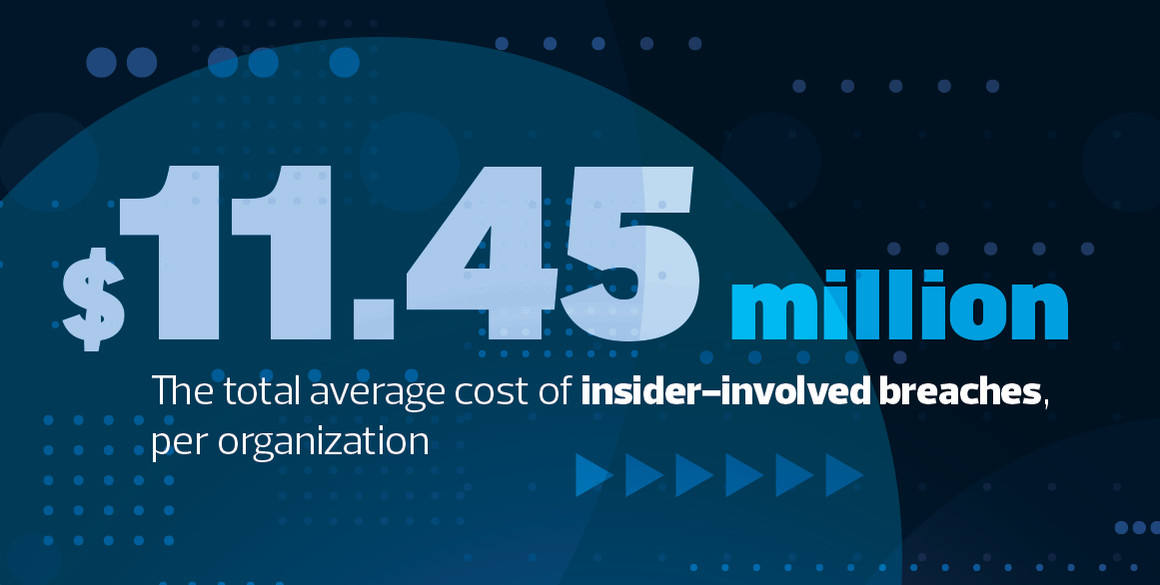
Organizations spend precious time building their business, gathering customer data and building trusting relationships. With the advances in cloud technology and networking, protecting your networks from breaches has never been more important. Cybersecurity protects important client data and defends IT from attack.
Take the Next Step in Your Zero Trust Journey
Close


Become an Insider
Unlock white papers, personalized recommendations and other premium content for an in-depth look at evolving IT
Copyright © 2024 CDW LLC 200 N. Milwaukee Avenue, Vernon Hills, IL 60061
Do Not Sell My Personal Information